Dest0g3 520迎新赛
目录
警告
本文最后更新于 2023-01-29,文中内容可能已过时。
misc
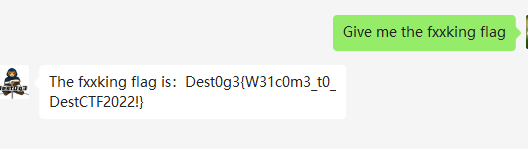
Welcome to fxxking DestCTF
关注公众号
Pngenius
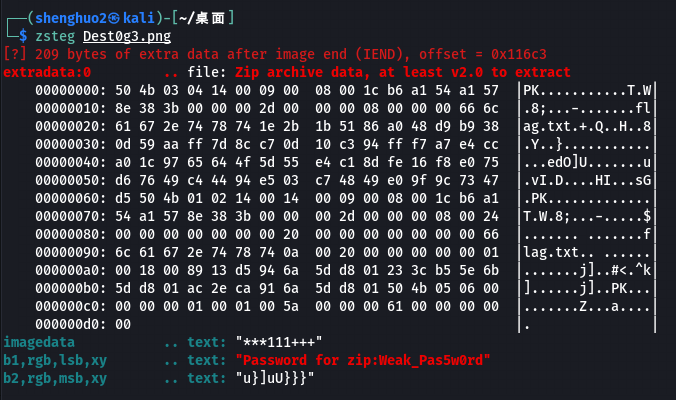
zsteg一把梭
binwalk分离压缩包 密码是Weak_Pas5w0rd
EasyEncode
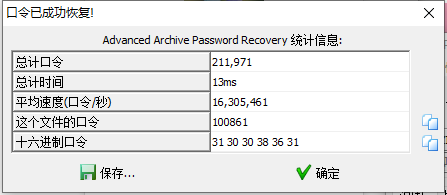
压缩包 爆破密码
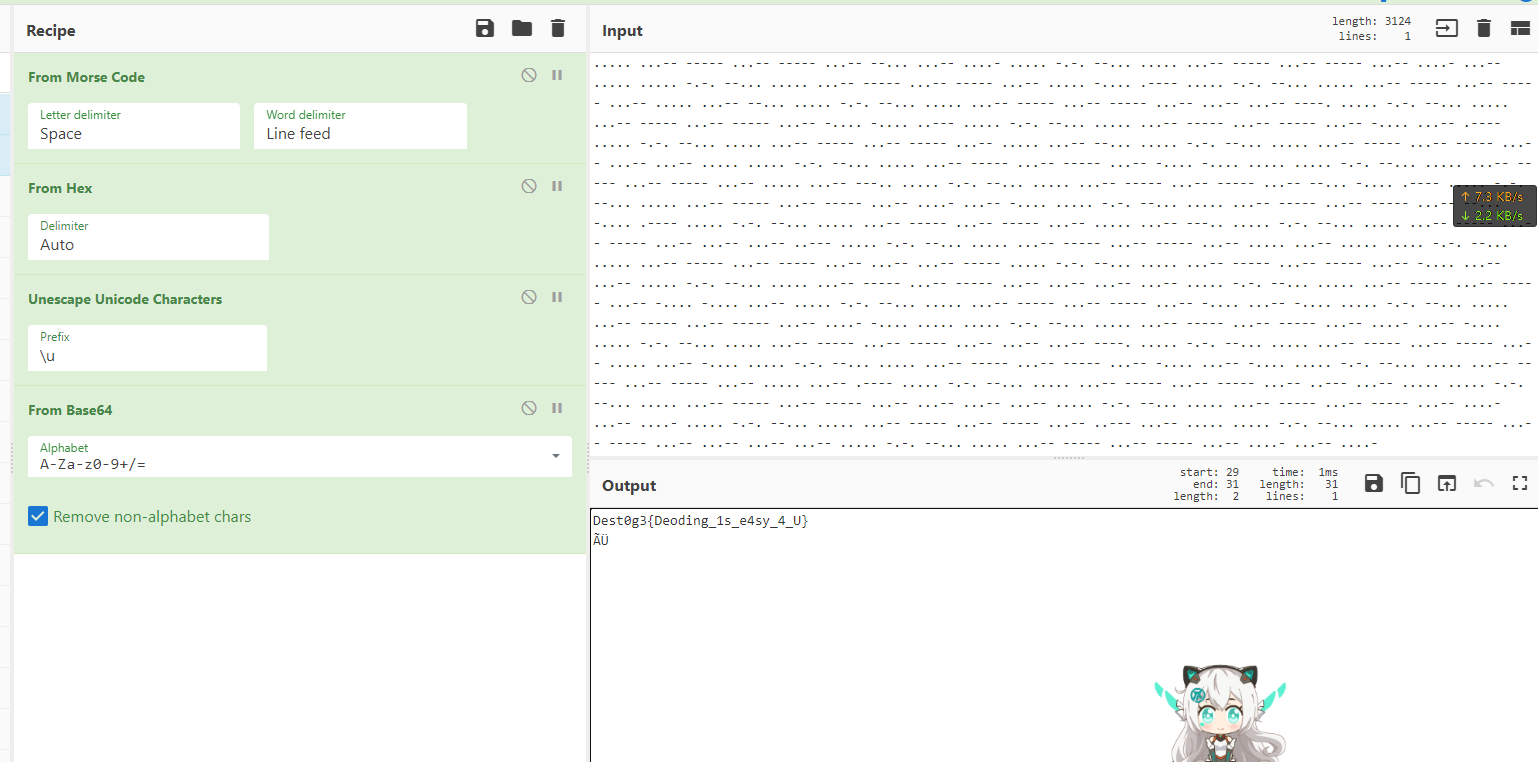
然后morse hex unicode base64套娃
cyberchef一把梭
RE
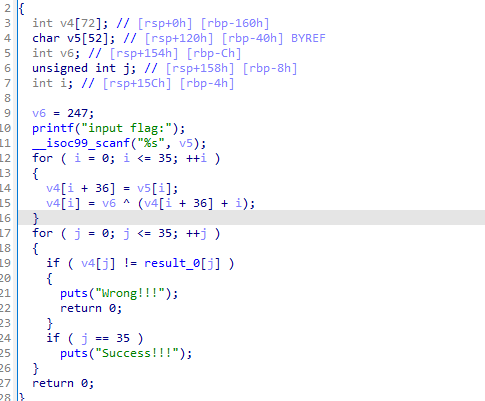
simpleXOR
提取出来result_0
然后异或247-i
|
|
Dest0g3{0bcgf-AdMy892-KobPW-hB6LTqG}
WEB
phpdest
开了半个小时开的靶机还进不去
又开了半个小时
|
|
wmctf2020的原题
文件上传+条件竞争 直接上脚本
|
|
EasyPHP
|
|
报错回显
post传个数组就行
|
|
SimpleRCE
|
|
绕过滤
hex2bin绕构造system
发现flag在根目录
head输出
|
|