ACTF个人能力认证考核WP
目录
警告
本文最后更新于 2023-02-01,文中内容可能已过时。
misc
mahjoong
就打开自动对战 挂着就行
胜利就有flag
|
|
emoji
emoji进行base100解密
得到一串0和1
转成hex
|
|
然后转成字符串
|
|
倒序再包上ACTF{}
|
|
web
babyshiro
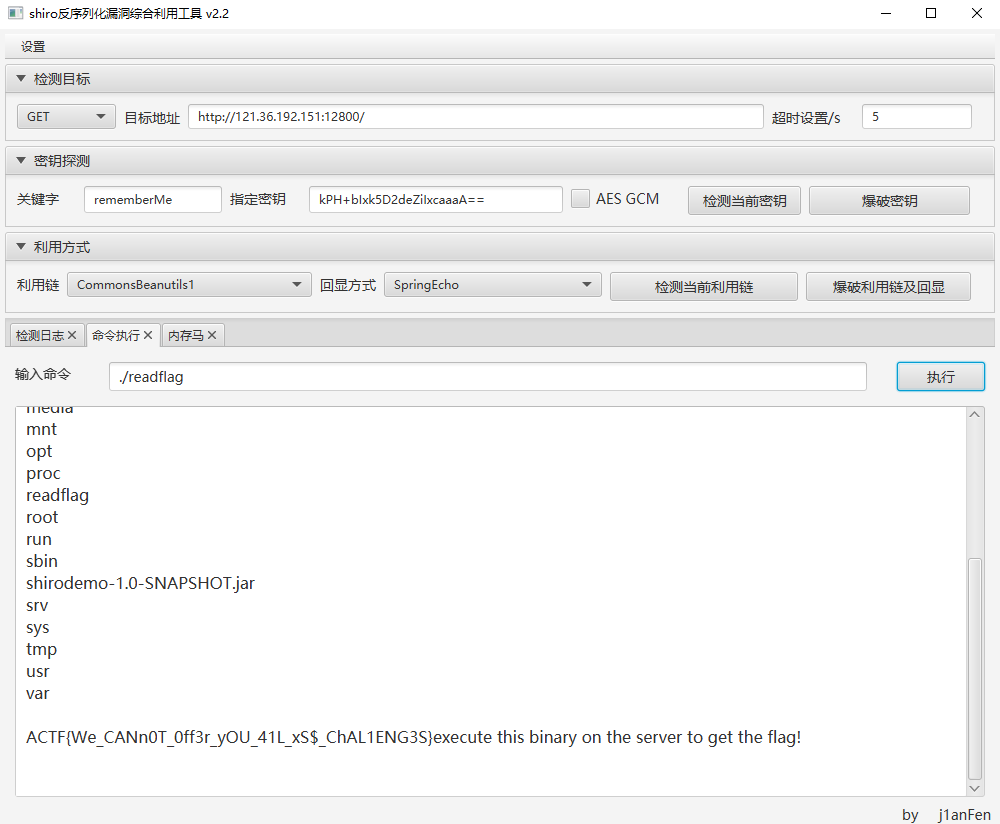
shiro反序列化漏洞命令执行
直接上工具就行
https://github.com/j1anFen/shiro_attack
re
crackme
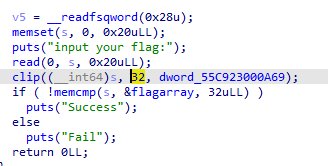
IDA反编译
先对输入的数据8位一组存进内存 intel是小端序 所以需要倒回来
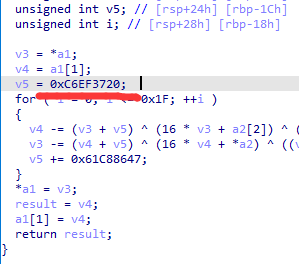
下一个函数里面看到 0xC6EF3720 是TEA算法
有两段值判断为解密函数
程序逻辑是把输入的数据进行分段加密后 进行解密
再与程序中存储的数据进行比较
所以要先对数据小端序读取,然后加密
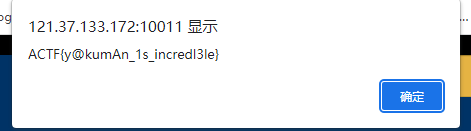
得到的就是flag
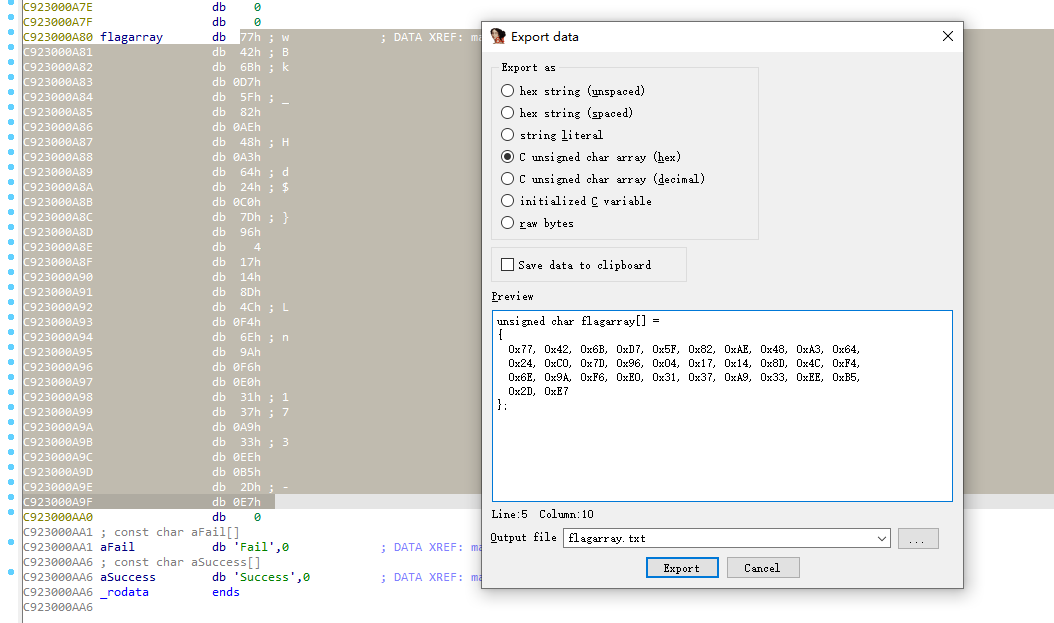
提取数组
|
|
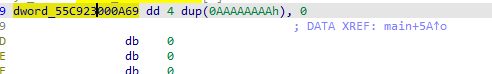
密钥是四组AAAAAAAA
tea加密 分段处理
|
|
|
|