NEPCTF 2022 WP
NepCTF 2022 wp
misc
花花画画画花花
Author: β-AS
花花画了一张图,你能看出来她画的是什么吗
(flag格式为NepCTF{})
解压得到一个osu!的谱面 人太菜打不过()
导入osu开个不会fail的模式读谱即可
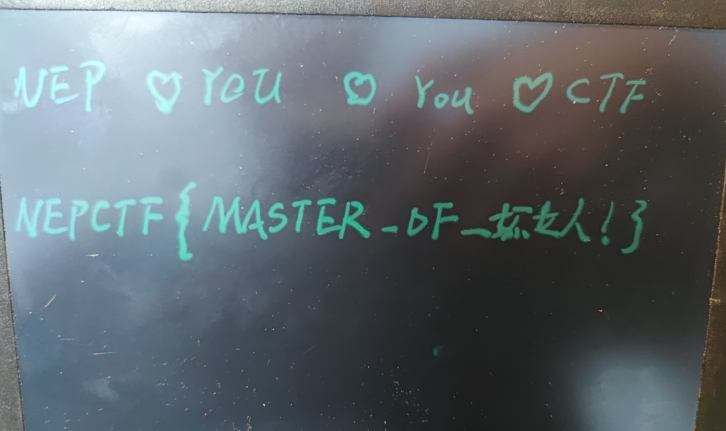
对着回放打的
签到题
Author: limu
极限套娃
flag格式为nepctf{}
换过压缩包之后就有思路了 解压缩包套娃 没有密码
参考贝塔师傅的脚本
|
|
解到最后得到1.zip
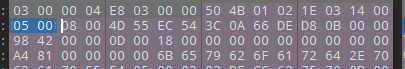
里面有一个显示加密的流量包 发现为伪加密 将deFlags从05改成00即可解压
一个键盘流量
先把流量提出来
|
|
然后用这个脚本
|
|
有点小问题 删一下重的字符就行
|
|
少见的bbbbase
Author: β - AS
少见的bbbbase
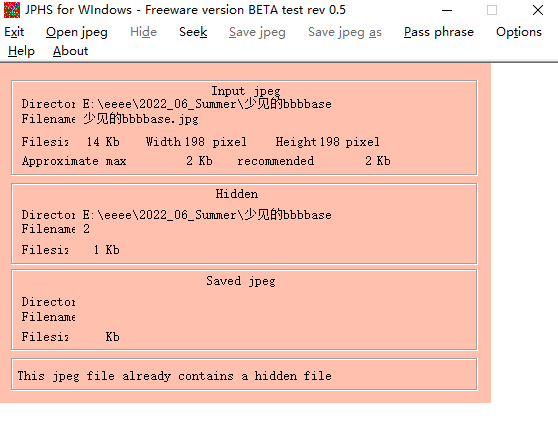
这是第一次用jphide解出来题
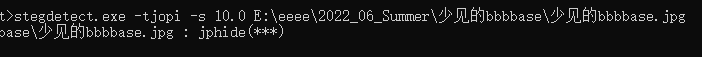
stegdetect检测
用jphs5解文件
得到文件 打开为一串base58
|
|
解base58得到flag
|
|
9点直播
Author: 花花~
各位同学,比赛已经开始将近十个小时啦,大家玩的如何呢?邀请大家9点来直播间聊聊天~ 请锁定https://b23.tv/bn0pPAR 这边小助手收到了大家想暴打出题人的反馈,今晚9点我们请到了变态的出题人们,在直播间和大家交流,放出我们的hint,帮助大家解题。 同时也会在直播间中抽幸运的小伙伴送出我们的周边礼品。
直播间得flag
|
|
馅饼?陷阱!
Author: Zuni
好兄弟中奖了,但是要先汇款。他去哪了?
NepCTF{银行官网网址}
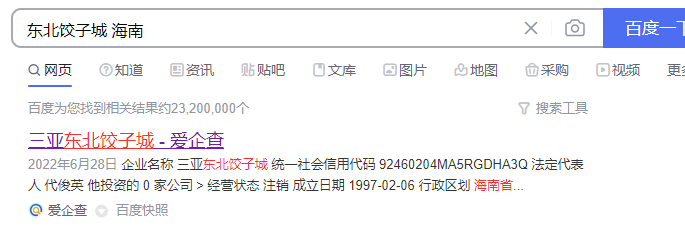
第二张图里能看到车牌号是琼 可以知道为海南
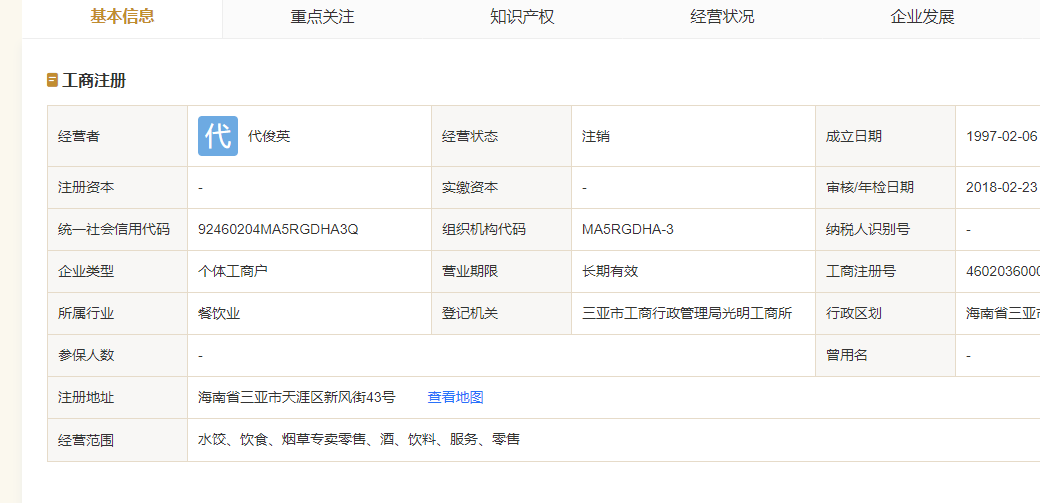
搜索东北饺子城 海南
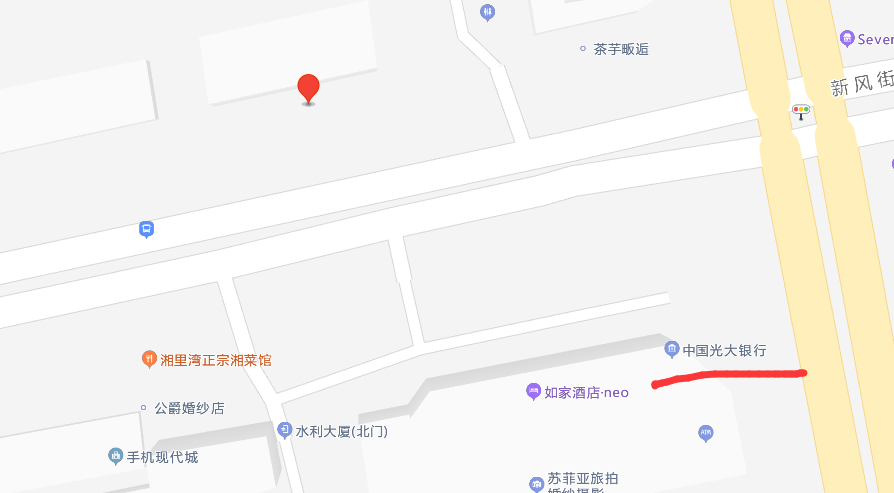
查看地图 可以使用全景地图看到相同风景
搜索广大官网得到flag
|
|
问卷
|
|
RE
快来签到
Author: emtanling
x86 linux
一个纯脑洞题
flag在Graph里
|
|
web
Just Kidding
Author: H3h3QAQ
顽皮的HRP用Laravel写了个项目来欢迎大伙来玩Nepctf 2nd,没想到…居然被坏蛋Sharun撅了
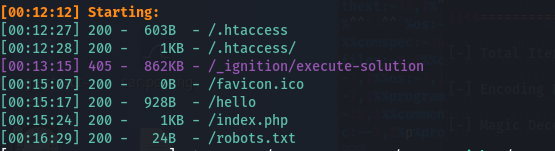
能扫出来几个目录和备份文件
根据备份中Laravel版本9.20可以找到一个最新的洞Laravel 9.18反序列化命令执行
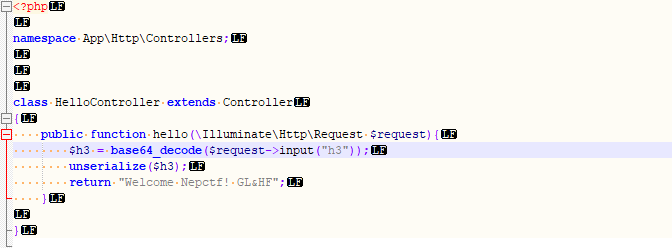
然后去搜hello能找到hello的文件位置 可以得到他的参为h3
构造一条链子传到h3就行
链子
|
|
|
|
Challenger
Author: H3h3QAQ
顽皮的HRP又换了种语言写项目来欢迎大家,没想到又让Sharun掘了