HGAME WEEK1 Re WP
目录
警告
本文最后更新于 2023-02-01,文中内容可能已过时。
为什么只有re,因为别的方向懒得写了( 也没做几题
Reverse
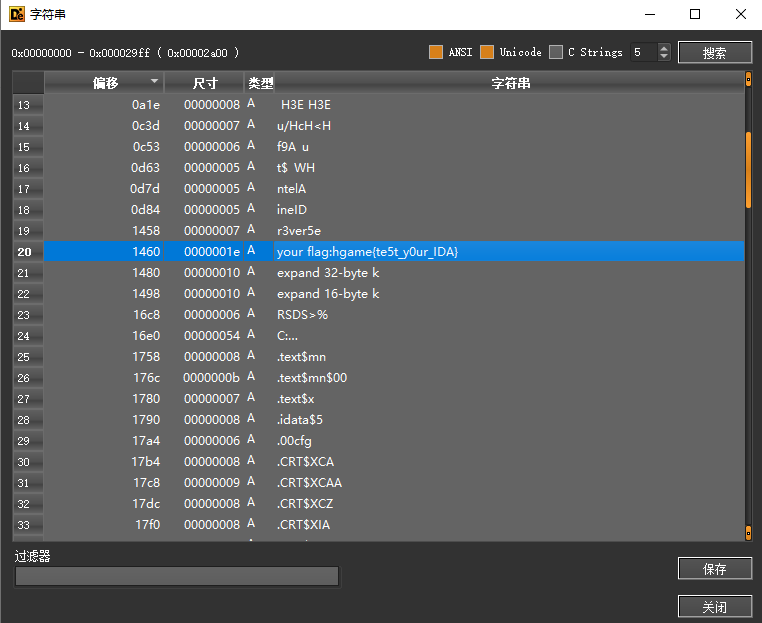
test your IDA
|
|
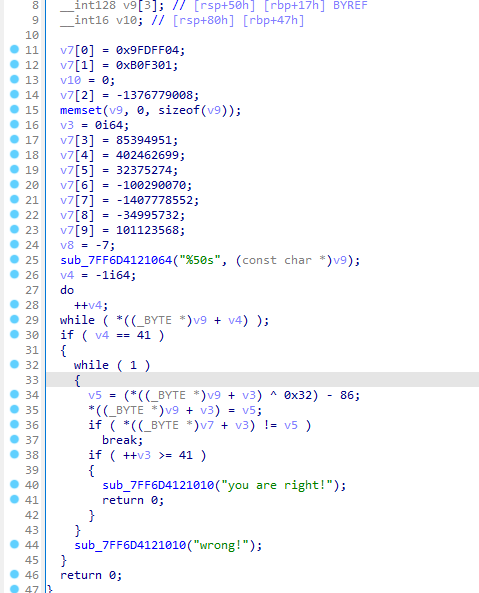
easyasm
给了段汇编代码,以及加密后的密文
重点是这句
|
|
异或0x33
|
|
不知道为什么忽然喜欢写一行了(
|
|
easyenc
搞了半天发现是漏了个0x00
但是我确实动调不起来
|
|
|
|
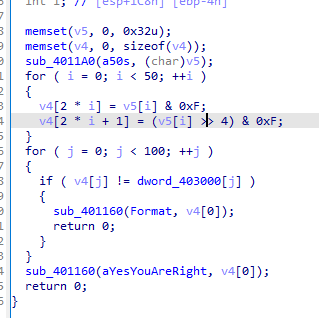
encode
就是把flag每位拆成高4b和低4b
分别存储为[i*2+1]和[i*2]
还原回来就行
|
|
|
|
a_cup_of_tea
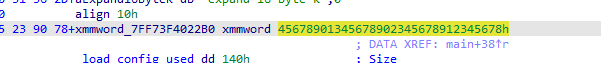
tea
key
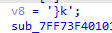
flag最后一段
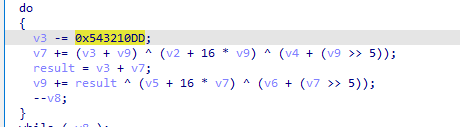
delta=0x543210dd
++-,没给sum,是加密函数
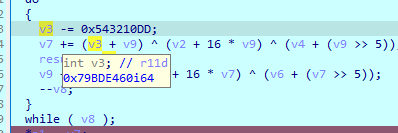
反过来写解密函数
动调到最后一轮得到sum
|
|
|
|