NepCTF 2024 wp
推测出题人的预期解,详细写了写区块链
misc
Nemophila
所以镜莲华的花语是?
二血
|
|
|
|
第4个字母没有提示,根据语义猜测是r
然后密码不是通过所有条件,而是exit在最后一个
|
|
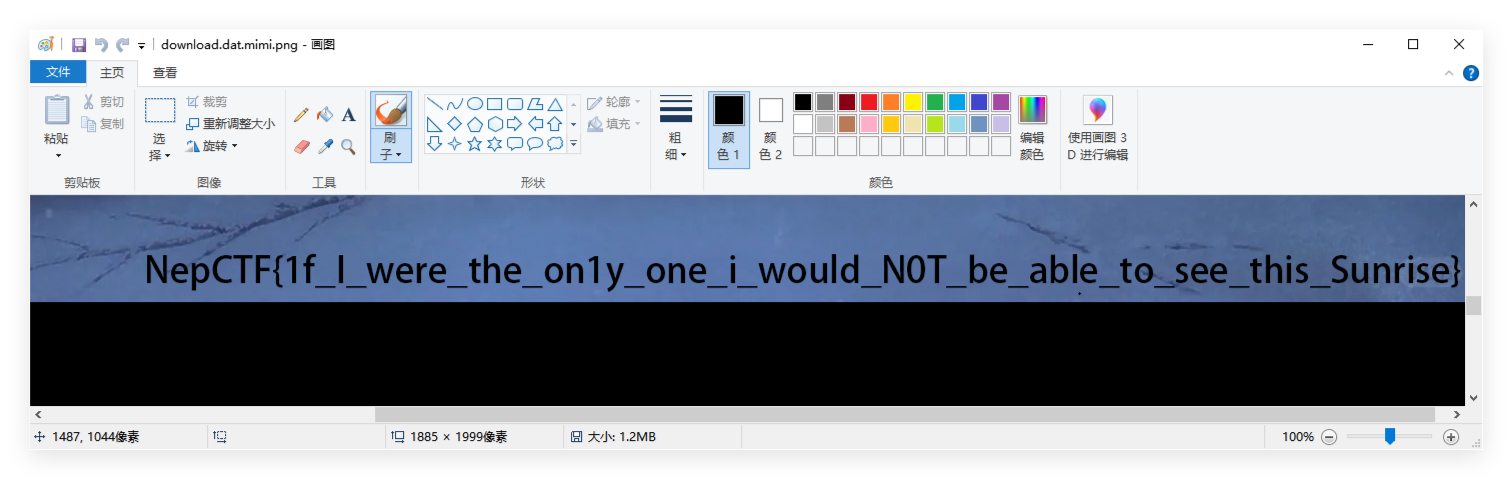
密码是
|
|
解压后拿到一个png,但是乱码
xor png头可以发现xor的key还是密码
然后再改大图片高度
|
|
3DNep
二血
文件头,glTF
找个在线预览
https://products.aspose.app/3d/zh-cn/viewer/gltf
底部是汉信码
调色一下
|
|
blockchain
theif_god
容器启动后3分钟再进行攻击 题目只提供部分合约部署代码以及攻击者账户密钥
Tips:本次区块链题目 只是为了让大家多多少少都接触下WEB3 ,题目本身没有很难 属于签到难度,只需在线即时学习即可完成。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24from web3 import Web3 # 连接到本地节点 web3 = Web3(Web3.HTTPProvider("https://neptune-xxxxx.nepctf.lemonprefect.cn")) # 定义一个函数来扫描区块链并查找合约创建交易 def find_contract_addresses(start_block, end_block): contract_addresses = [] for block_number in range(start_block, end_block + 1): block = web3.eth.get_block(block_number, full_transactions=True) for tx in block.transactions: if tx.to is None: receipt = web3.eth.get_transaction_receipt(tx.hash) contract_addresses.append(receipt.contractAddress) return contract_addresses # 扫描区块范围 start_block = 0 # 起始区块 end_block = web3.eth.block_number # 当前最新区块 contracts = find_contract_addresses(start_block, end_block) print("Deployed contract addresses:") for address in contracts: print(address)附件:https://pan.baidu.com/s/1vuzalD8A3BKpQWYnoqOB3A?pwd=s5o6
题目附件里面可以看到合约部分
|
|
很明显的重入攻击
在 hardhat.config.js 可以看到一个priKey,该账户里面有10ether
|
|
题目描述
https访问:
|
|
说明是RPC
geth连不上rpc,那就用web3.py
做法1
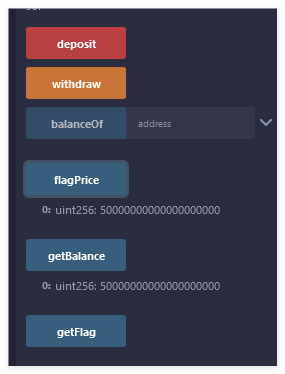
可以发现flag直接就在slot1里,虽然直接读slot读不到(
|
|
读block
|
|
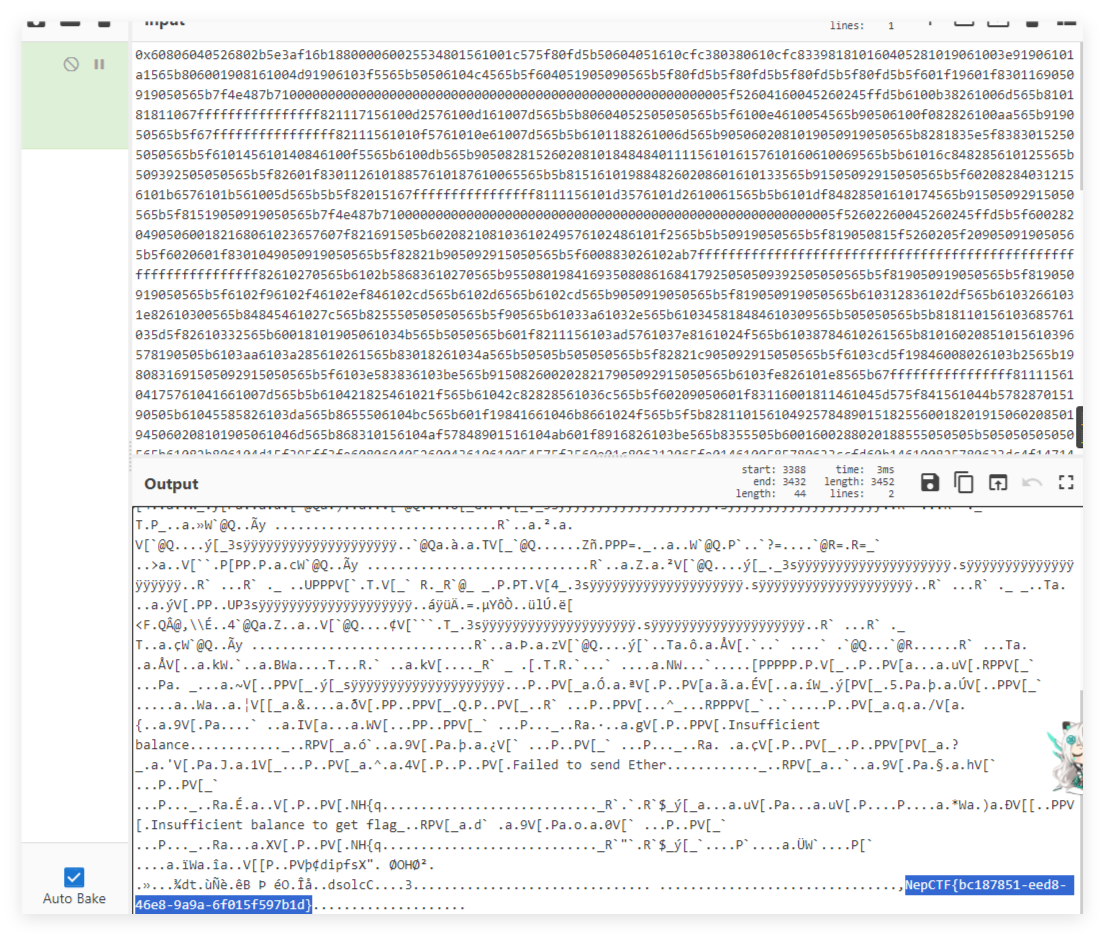
直接看input
做法2(预期解)
题目最早是没给任何提示的
先摸索出动态靶机是rpc
然后再写脚本读
其实一共就四个block
|
|
|
|
其实block 2的也有一个合约
用来给Bank.sol存入初始的50eth,用于完成攻击
所以重入是为了取出他人存在合约里的余额
getBalance可以看到里面有50Ether
不过题目环境很卡(
|
|
重入攻击的原理是由于目标合约通过msg.sender.call{value: balance}("")的方式转账
且先转账再减钱
fallback()的特点 在合约调用没有匹配到函数签名,或者调用没有带任何数据时被自动调用。
所以这题如果在fallback里面写withdraw()会被反复触发,也就是重入
部署攻击合约
往exp合约存一点,1 Gwei也行
然后打attack重放
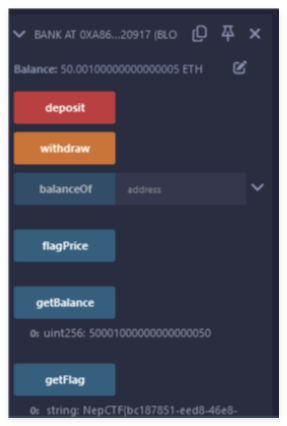
会把里面的50eth都取出到exp合约里
再把钱提到账户里,存回到题目合约里
满足条件,拿到flag