警告
本文最后更新于 2024-08-20,文中内容可能已过时。
DASCTF 2024暑期挑战赛|为热爱,并肩作战
png_master
第一部分
文件尾解base64
1
2
|
Congratulations on finding the first paragraph of flag, but the understanding of png is just beginning.
flag1:DASCTF{2fd9e9ff-e27
|
第二部分
仔细看图片,可以发现

每4个像素一组,有一组是A通道比较明显的
拆成四个图片再读取也行,直接上stegsolve读取也行

拆开是这个样子
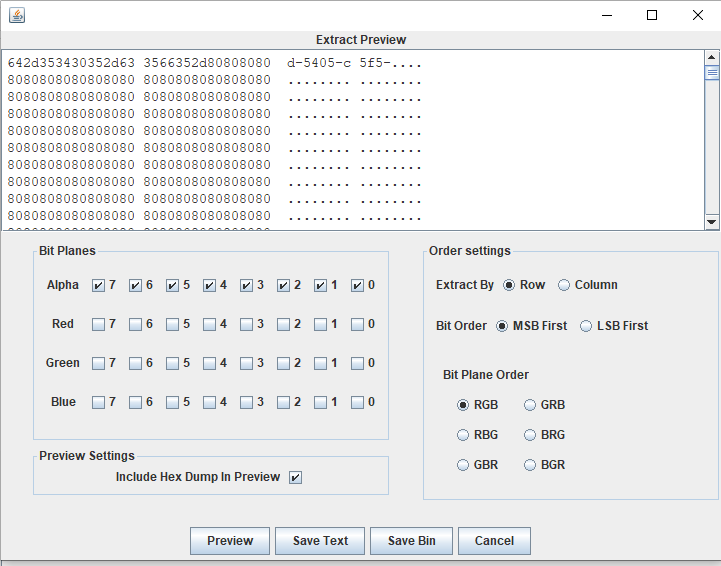
或者写用脚本读取
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
from PIL import Image
import numpy as np
def get_alpha_channel_integers(image_path):
img = Image.open(image_path)
if img.mode != 'RGBA':
img = img.convert('RGBA')
alpha_channel = np.array(img)[:, :, 3]
alpha_channel_integers = alpha_channel.flatten()
return alpha_channel_integers
image_path = 'flag.png'
red_channel_binary = get_alpha_channel_integers(image_path)
print("".join([ chr(i) for i in red_channel_binary[:100] if i < 128]))
#d-5405-c5f5-
|
第三部分
zsteg会提示png最后有额外块
789c也是zlib的标志头
1
2
3
|
from PIL import Image
image = Image.open('flag.png')
image.save('copy.png')
|
读取再保存,可以发现最后的块没有了,说明这个块确实不正常
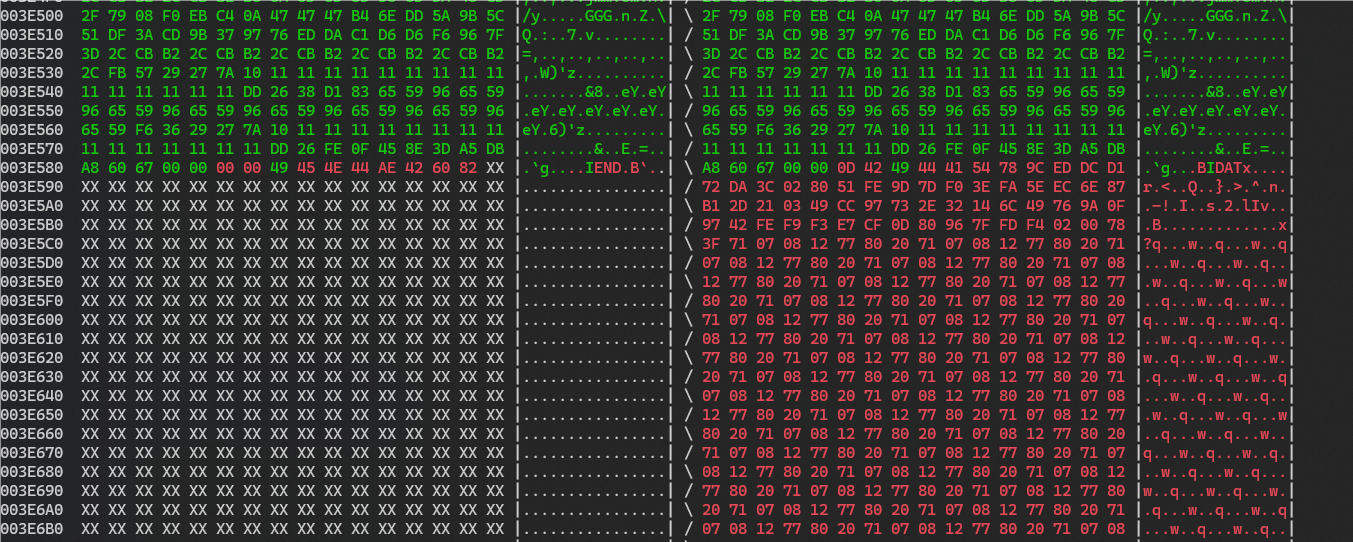
把这个块拿来当成另一个图片处理
补文件头,文件尾,
1
2
3
|
89 50 4E 47 0D 0A 1A 0A 00 00 00 0D 49 48 44 52
00 00 08 7A 00 00 04 38 08 06 00 00 00 7C 45 29
D5 00 00 0D 42 49 44 41 54
|
这一整个IDAT块,包括crc都弄过来
因为图片的crc未知
进行宽高的爆破,结果是500x500

1
|
DASCTF{2fd9e9ff-e27d-5405-c5f5-a19131f86216}
|
EZ_zip
手工修复flag_xxxxxxxxx.zip,010可以发现comment段被截断了
参照着DirEntry改动record段
改deFileNameLength为7,再把COMPTYPE deCompression改成COMP_DEFLATE (8)
(实测改成0会crc错误)(从压缩率来推断也不是0)
Comment:just a byte
然后根据comment提示,用字节形式的密码来爆破
python测了半天没成功,用hashcat验证一下猜想
1
|
hashcat -m 13600 -a 3 -i --increment-min=1 --increment-max=4 hash1.txt ?b?b?b?b
|
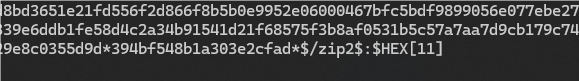
确实是byte形式的密码
再去尝试写脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
import io
import pyzipper
def ex(z, p):
try:
with pyzipper.AESZipFile(z) as f:
f.pwd = bytes.fromhex(p)
mf = {i.filename: io.BytesIO(f.read(i.filename)) for i in f.infolist()}
print(f"Pwd: {p}")
return mf
except:
return None
bf = lambda mf: next((ef for n, d in list(mf.items()) if n.endswith('.zip') for p in (f'{j:02x}' for j in range(256)) if (ef := ex(d, p))), {})
zip_file = '320.zip'
with open(zip_file, 'rb') as f:
d = io.BytesIO(f.read())
mf = next((mf for p in (f'{j:02x}' for j in range(256)) if (mf := ex(d, p))), None)
while mf:
if 'AES-ECB.txt' in mf:
[print(f"Saved: {n}") or open(n, 'wb').write(d.getbuffer()) for n, d in mf.items()]
break
mf = bf(mf)
|
用bytesIO把zip存到memory,减少硬盘IO导致的解压时长
1
|
python3 exp2.py 114.60s user 8.28s system 51% cpu 3:59.28 total
|
1
|
python3 exp4.py 34.97s user 0.03s system 99% cpu 35.010 total
|
快了7倍
(去掉print还能快一点)
运行320轮
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
|
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Pwd: 11
Pwd: bb
Pwd: 99
Pwd: 58
Pwd: 0c
Pwd: 61
Pwd: 3a
Pwd: 87
Pwd: c5
Pwd: 4e
Pwd: 12
Pwd: 48
Pwd: 0a
Pwd: a7
Pwd: ff
Pwd: 8c
Pwd: 79
Pwd: 8f
Pwd: 71
Pwd: ad
Pwd: 28
Pwd: 0f
Pwd: 6b
Pwd: a6
Pwd: 9d
Pwd: 4a
Pwd: 44
Pwd: 25
Pwd: 22
Pwd: 5e
Pwd: 4e
Pwd: c6
Saved: AES-ECB.txt
|
得到AES-ECB.txt
1
2
3
|
64ZpNmbv2Hg4Jj9bH8Kv6D3OBliD9hgyI3vZWfMDJs2TcEwVnBmH/zkBtPBE3g8e
the key may be on your journey?
|
再返回去处理输出的key
1
|
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
|
一共640个字符的hex,可以发现每64一组就刚好,而且每组一样
1
2
3
4
5
6
7
8
9
10
|
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
|
经测试,从0到320为正确方向
所以AES key为
1
|
c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
|
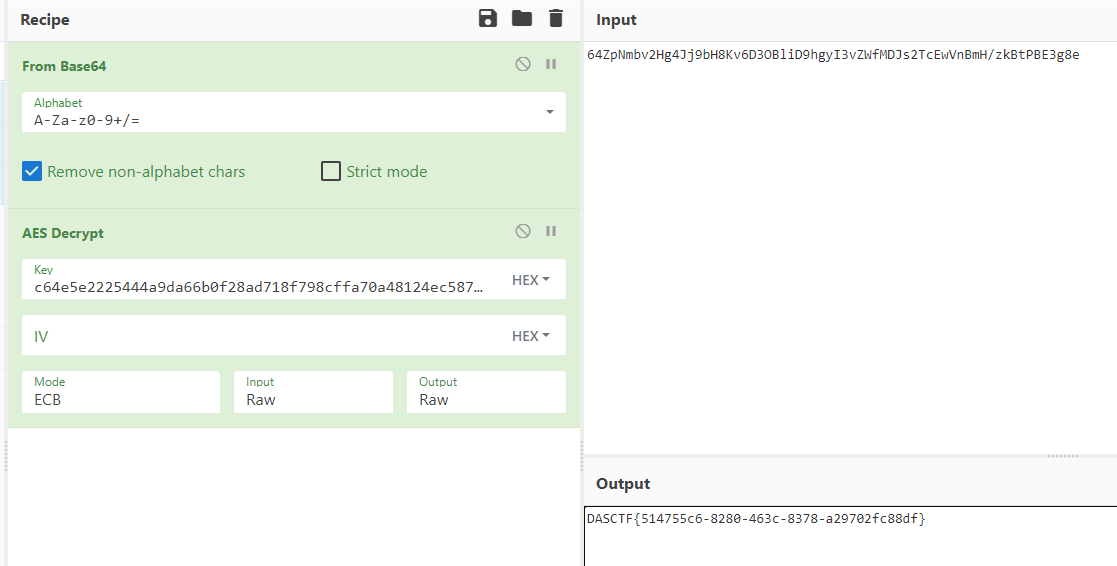
or
1
2
3
4
5
6
7
|
from Crypto.Cipher import AES
from base64 import b64decode
key = bytes.fromhex('c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11')
c = b64decode(b"64ZpNmbv2Hg4Jj9bH8Kv6D3OBliD9hgyI3vZWfMDJs2TcEwVnBmH/zkBtPBE3g8e")
cipher = AES.new(key,mode=AES.MODE_ECB)
print(cipher.decrypt(c).decode())
|
1
|
DASCTF{514755c6-8280-463c-8378-a29702fc88df}
|







