HDCTF 2023 writeup

RANK: 14

MISC
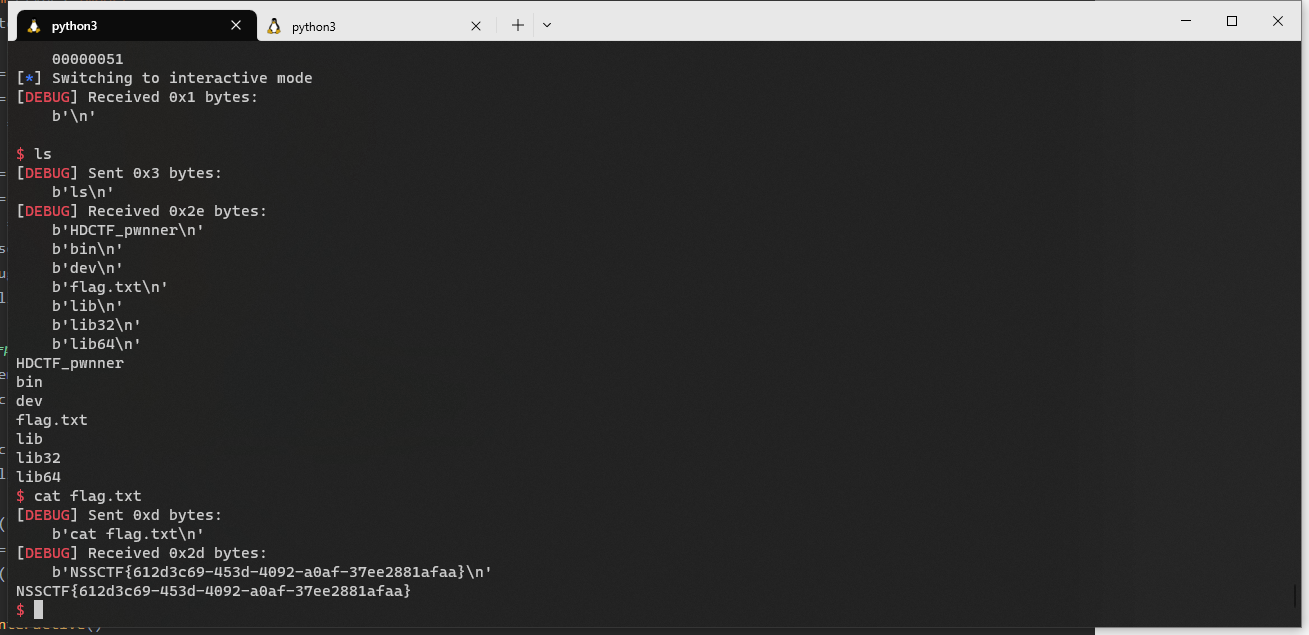
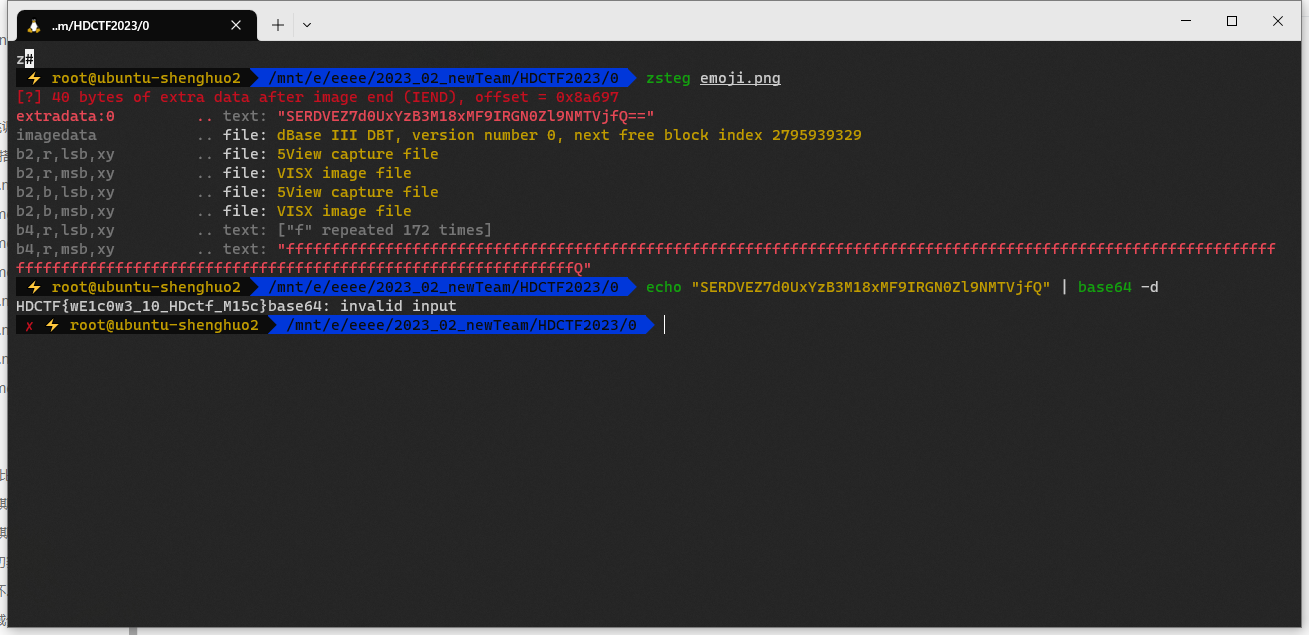
hardMisc
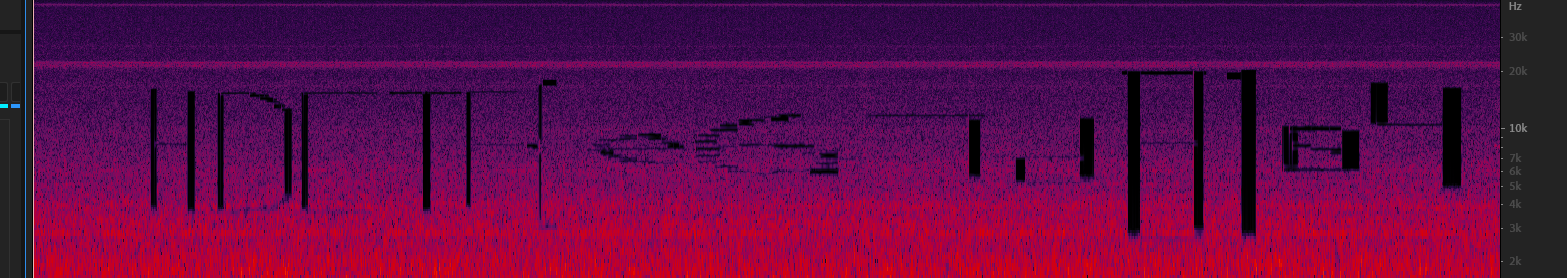
zsteg得到数据
解base64
|
|
ExtremeMisc
压缩包常规题型
IDAT.png文件尾分离出来zip
然后是Dic.zip,名字可知用字典爆破
用的rockyou.txt
然后,解两位一组倒序
|
|
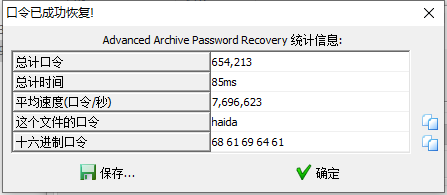
然后爆破密码
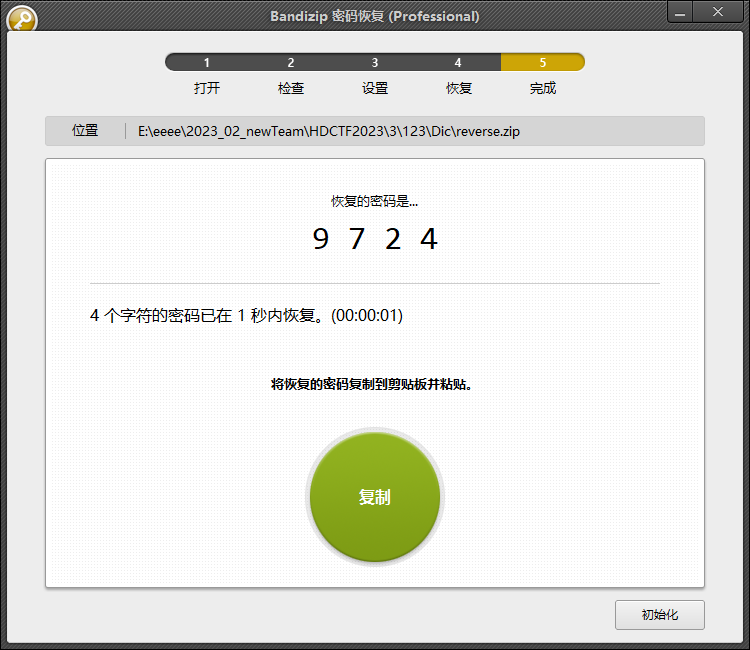
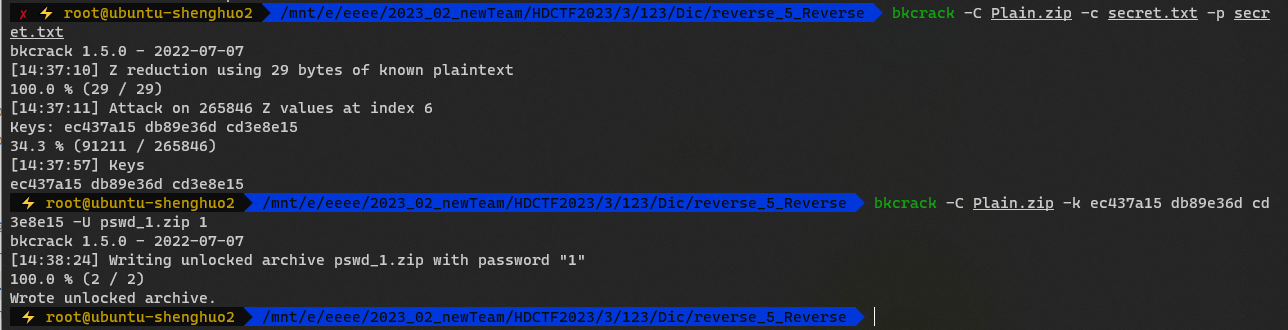
然后明文攻击
嫌archpr慢,用bkcrack爆破的
MasterMisc
带密码的分卷压缩
用bandizip高版本自带的密码爆破
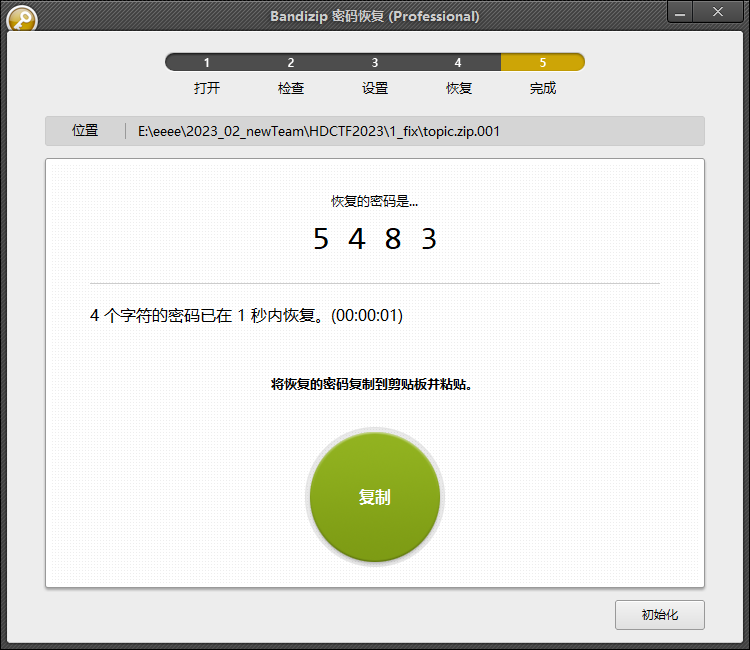
flag有三部分
topic.png后面有个png,然后还有个wav
在第二个png和wav之间有第三段flag
第二个图片高度有问题,改高后查看得第二个flag
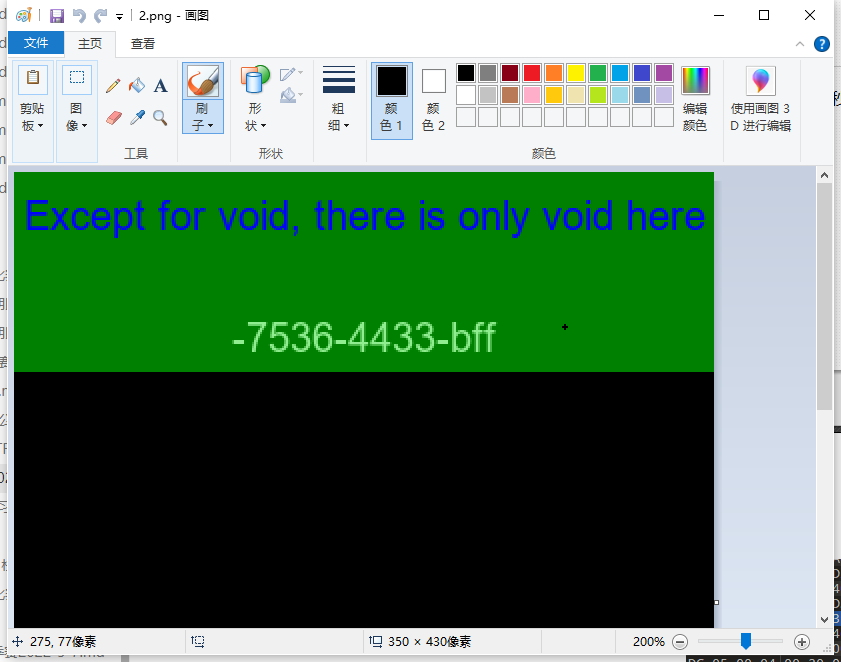
最抽象的是第一个flag
NSSCTF{e67d8104
|
|
Normal_Rsa
flag直接放在上面没删
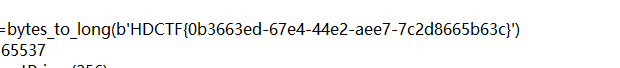
CRYPTO
Normal_Rsa
出题人忘了删flag了
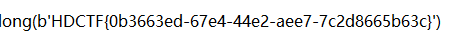
Normal_Rsa(revenge)
|
|
爬过小山去看云
山是hill密码
云是云影密码
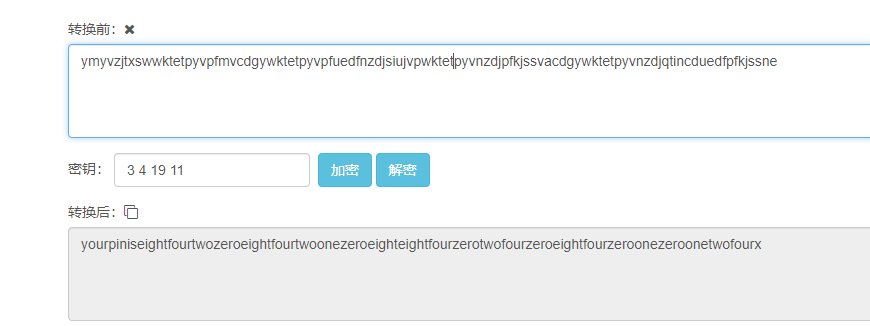
eight,four,two,one,zero换成84210
云影密码
|
|
差点以为做错了。
NSSCTF{NOTFLAG}
web
Welcome To HDCTF 2023
看源码找到game.js
找到这一串
放到控制台运行即可

SearchMaster
题目让post提交一个data
随便传一个在页面执行了

当传入{时他会报错,看报错信息发现
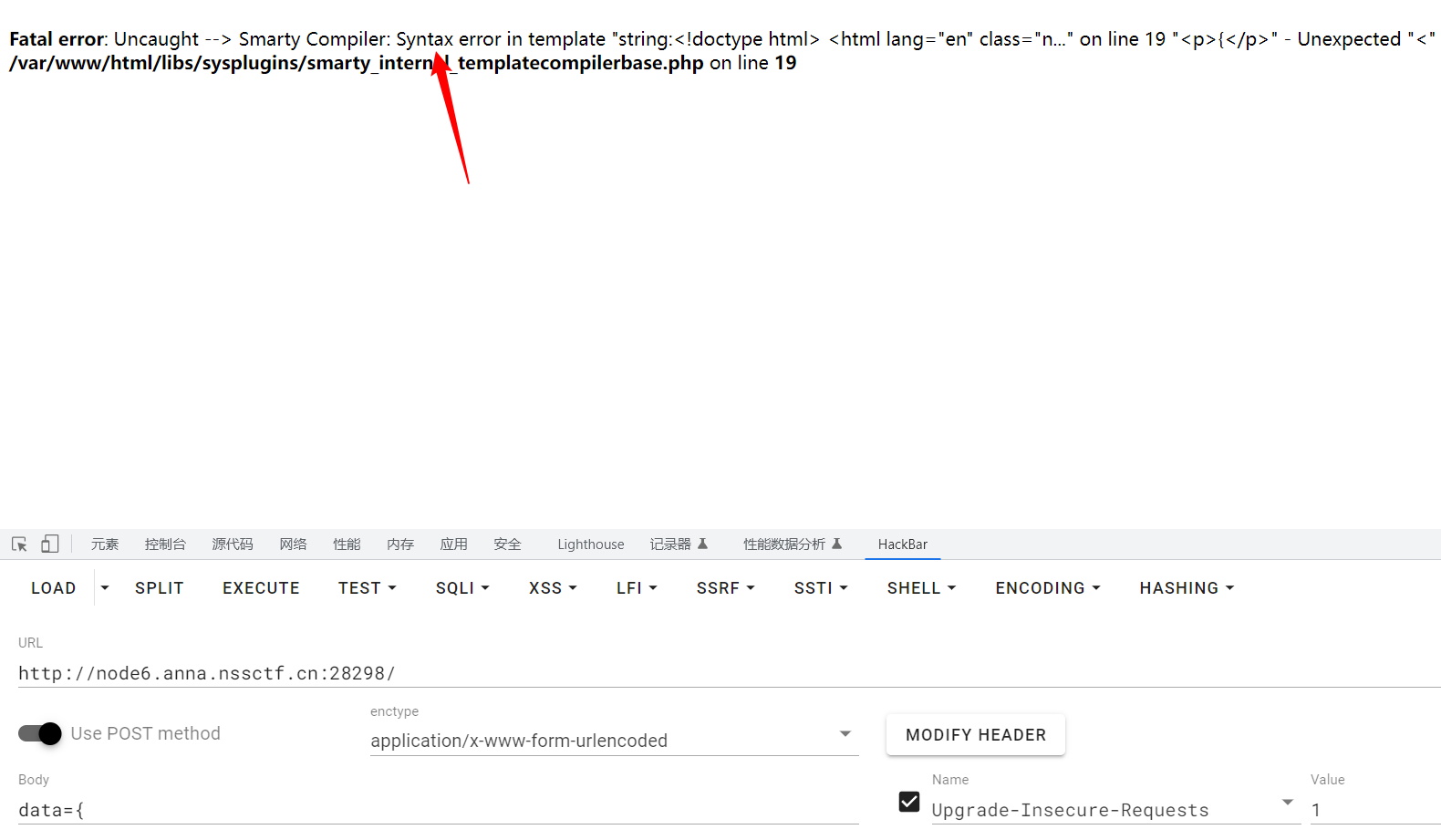
Smarty,猜测Smarty的ssti,数据发送到前端
用{if}标签即可
|
|
可以执行phpinfo()
直接命令执行即可
|
|
YamiYami
三个链接,点read somethings之后看url
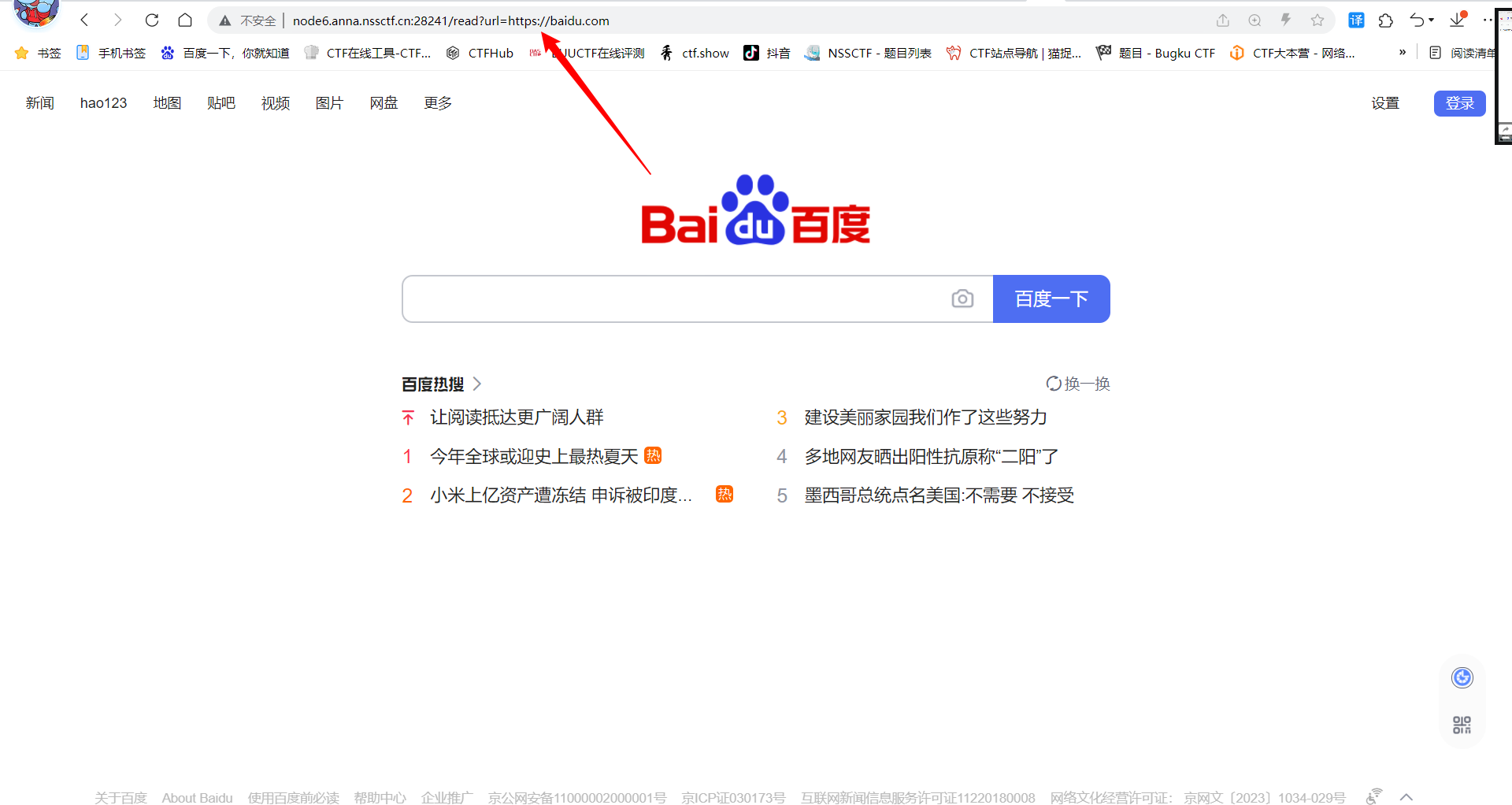
应该是ssrf尝试一下文件读取
|
|
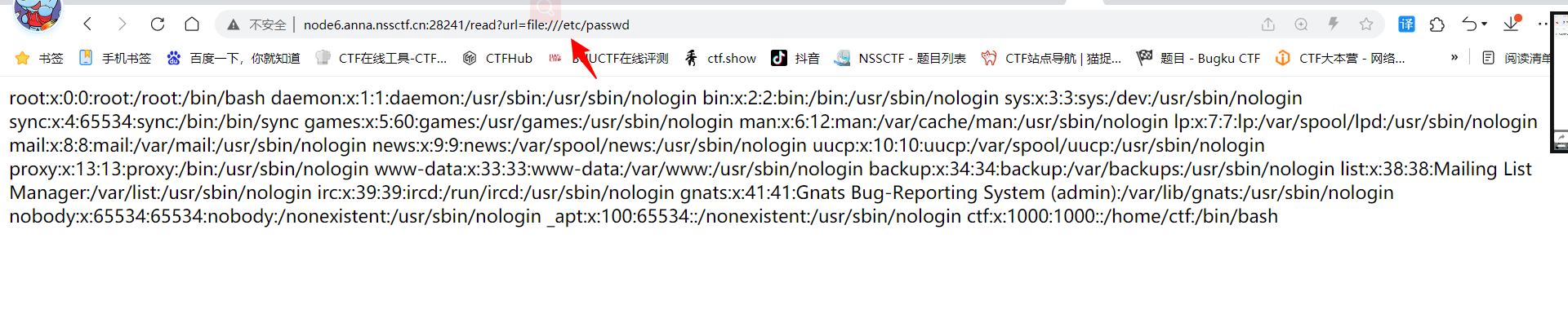
可以读,但不能读flag,尝试读环境变量
|
|
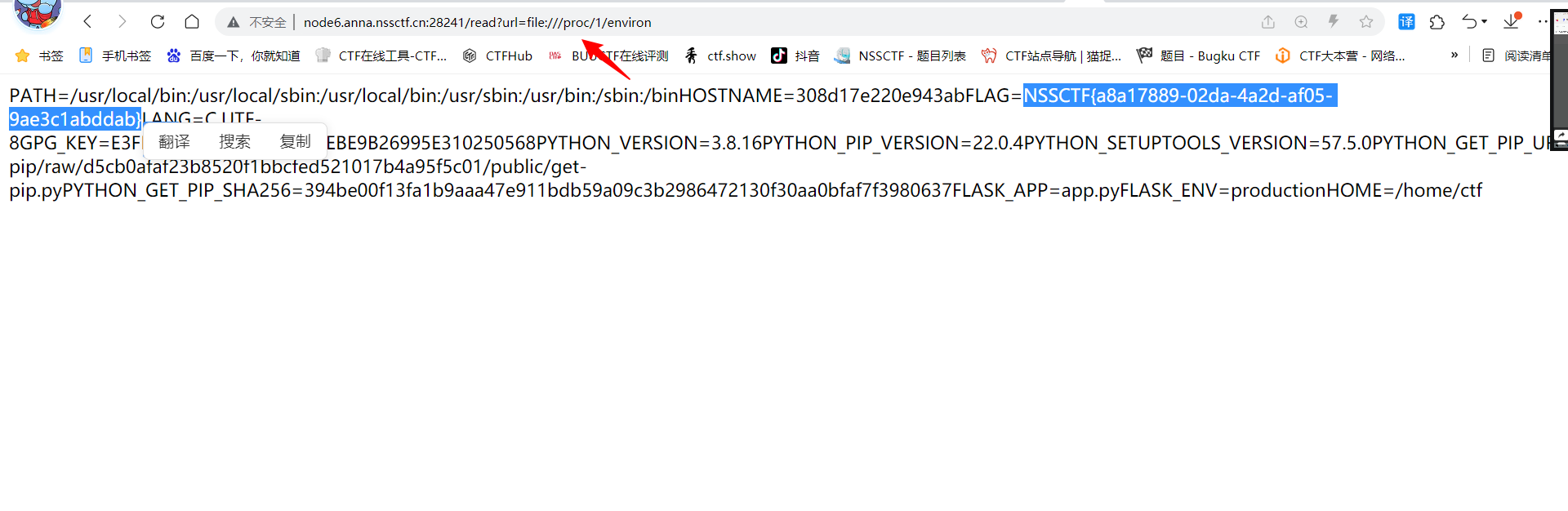
可以看到flag在环境变量中
LoginMaster
用dirsearch扫目录扫出
/robots.txt
|
|
构造一个查询结果是自身的sql语句
https://www.cnblogs.com/aninock/p/16467716.html
|
|
JavaMonster
jwt
将admin改成Boogipop解出jwt传入cookie:a=1;b=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2ODIxNzcxMTgsImlhdCI6MTY4MjE2OTkxOCwidXNlcm5hbWUiOiJCb29naXBvcCJ9.1dfoUuPRgwflPRL8beAumUMOCVFIRCV4yAjXd18Syko
|
|
hashcode
USy to solve EasyJava的hash等于Try to solve EasyJava
rome二次反序列化
将结果带入dnslog
|
|
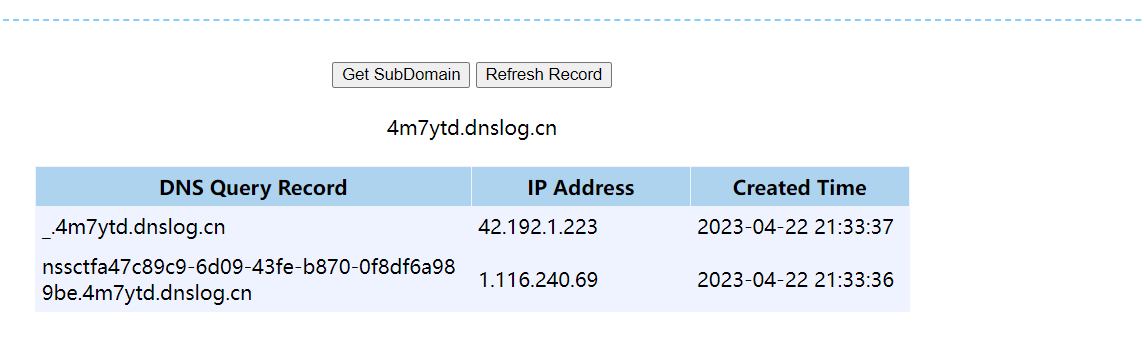
REVERSE
easy_re
先脱upx壳
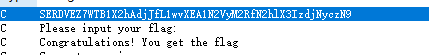
|
|
一眼base64
解码得flag
|
|
easy_asm
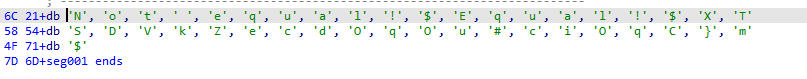
这是数据段
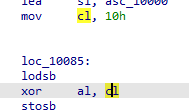
重点就是
|
|
异或0x10
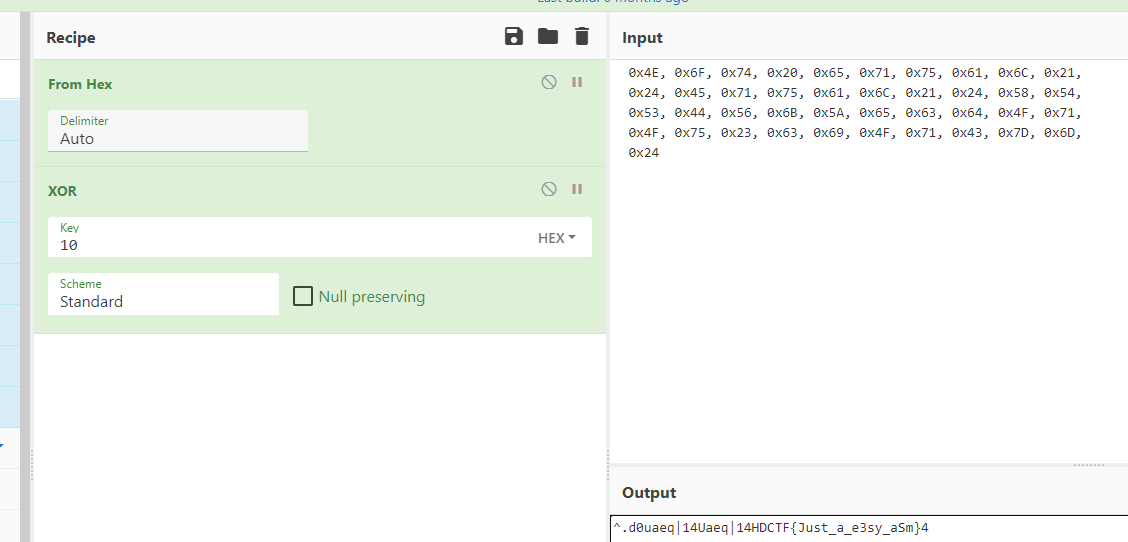
|
|
fake_game
pyinstxtractor反编译exe
用这个项目的,可以自动帮你补全结构头,不用再修
https://github.com/pyinstxtractor/pyinstxtractor-ng
uncompyle6反编译pyc
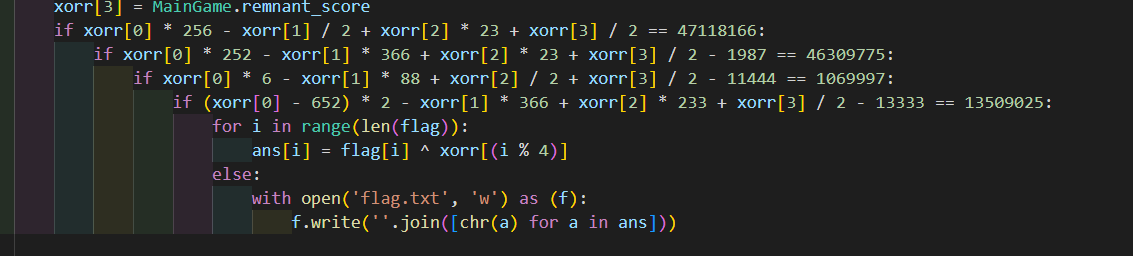
关键函数部分
用sage解方程式
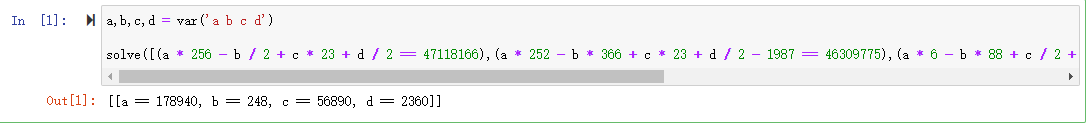
如果xorr[3]=2360
解出来的flag不对
|
|
反过来根据flag的格式推xorr[3]
|
|
可知xorr[3]应为2361
|
|
买了些什么呢
flag以NSSCTF形式提交,商品的编号从小到大排列(用空格隔开例如NSSCTF{1 2 3 40})即为flag
hint: [HDCTF 2023]买了些什么呢商品下标从0开始
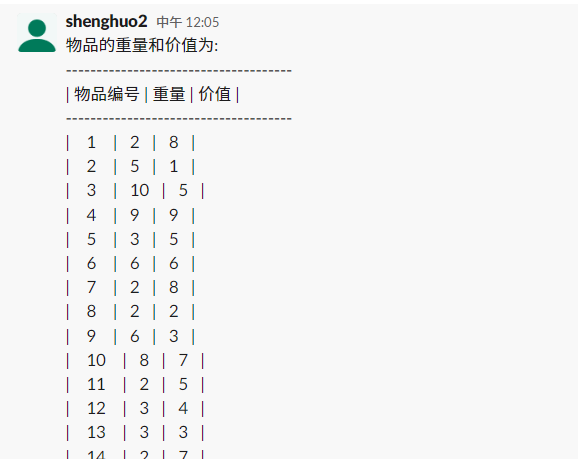
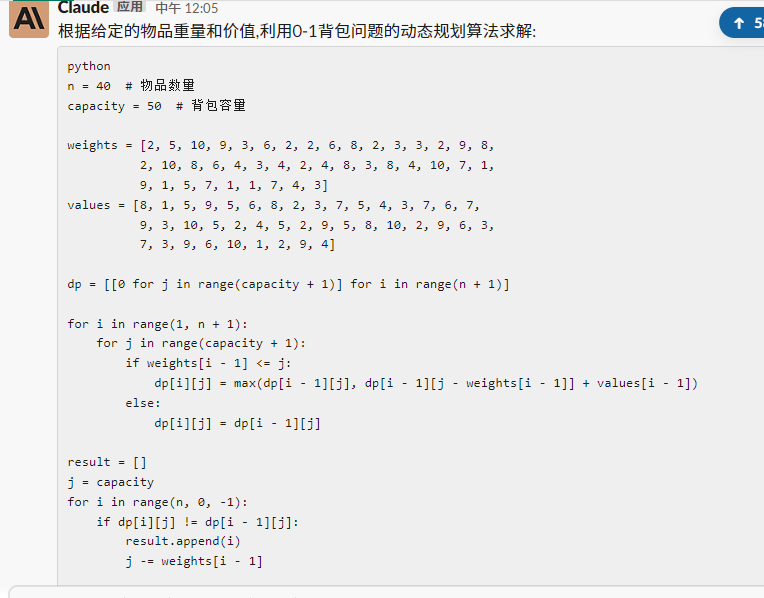
直接交给Claude
|
|
结果是
|
|
根据提示改一下
|
|
|
|
PWN
pwnner
|
|