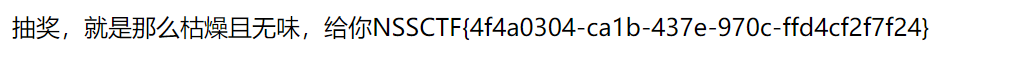NSSCTF平台 密码刷题记录

目录
警告
本文最后更新于 2023-04-18,文中内容可能已过时。
做了一些MT 之类的伪随机数生成器
密码入门
[SWPUCTF 2021 新生赛]crypto8
uuencode
uu库其实调用的是binascii的函数(
|
|
[SWPUCTF 2021 新生赛]crypto7已解决
somd5查询
|
|
[强网拟态 2021]拟态签到题
解base64
|
|
[鹤城杯 2021]A_CRYPTO
base+rot13
|
|
常用编码
[BJDCTF 2020]base??
|
|
NSSCTF{D0_Y0u_kNoW_Th1s_b4se_map}
伪随机
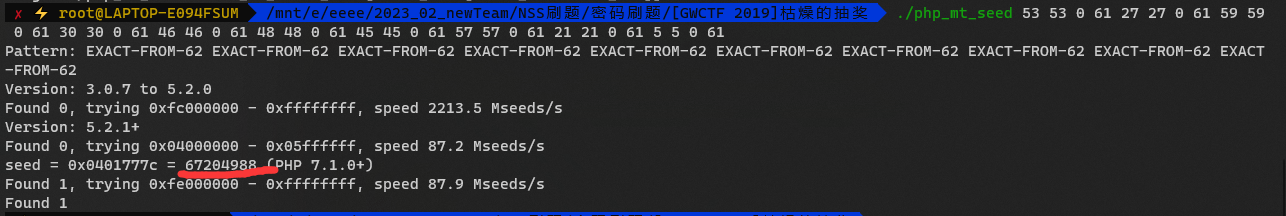
[GWCTF 2019]枯燥的抽奖
|
|
|
|
|
|
R1X4KMJVvflgWwhsgen0
POST:num=R1X4KMJVvflgWwhsgen0
[PASECA 2019]Tornado_Casino
|
|
|
|
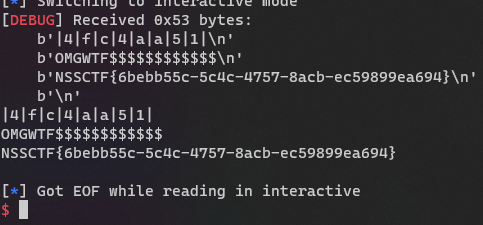
[GKCTF 2021]Random
最简单的预测题
|
|
NSSCTF{14c71fec812b754b2061a35a4f6d8421}
[天翼杯 2021]babypack
太难了😭
春哥的exp:https://zhuanlan.zhihu.com/p/413319231
[HGAME 2022 week4]PRNG
简单的MT
|
|
[长城杯 2021 政企组]魔鬼凯撒的RC4茶室
|
|
|
|
另外半段有关rc4的部分
|
|
|
|
rc4的%256
直接xor爆破也是能得到结果的
|
|